IT Vulnerability Assessment Template
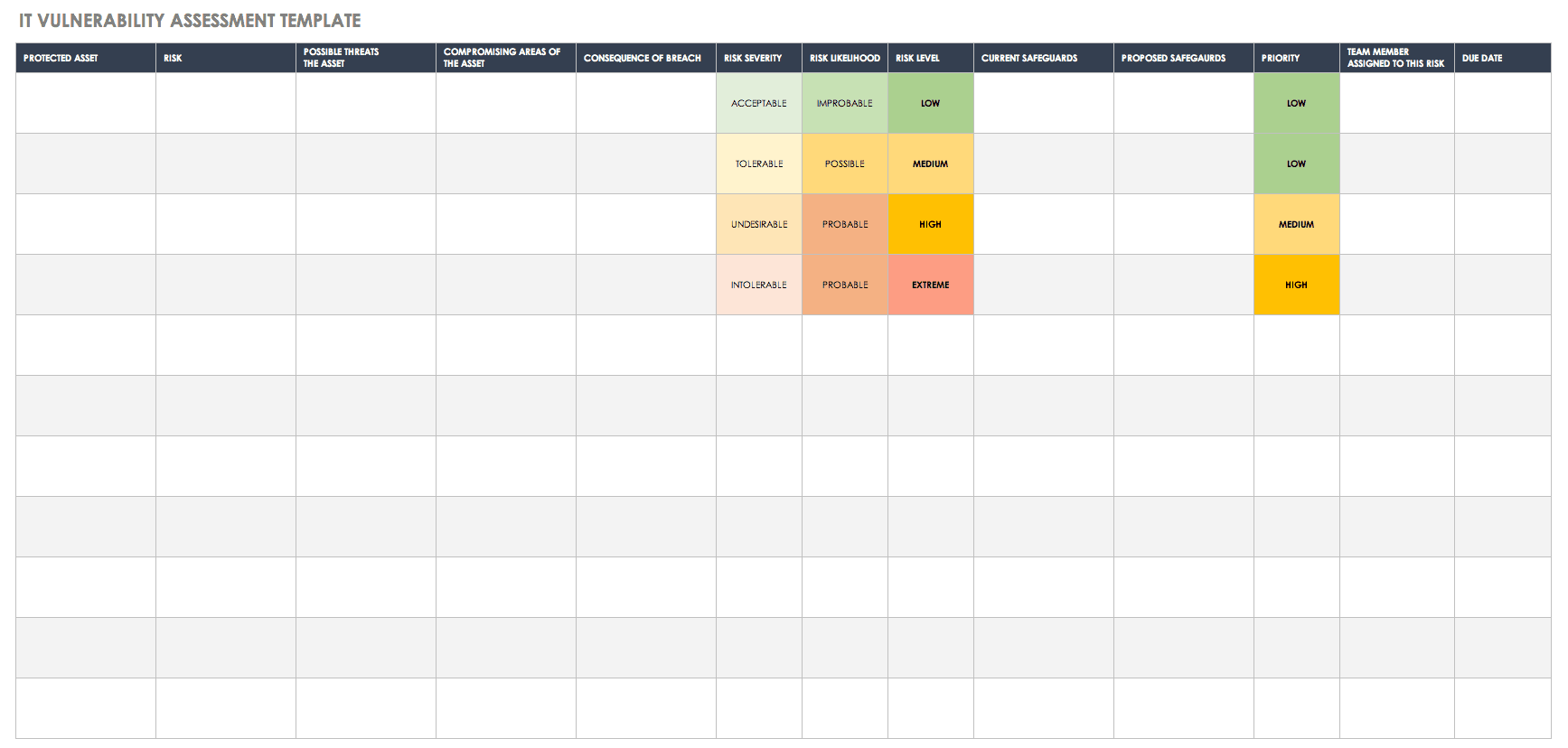
This template is designed to help you identify and deal with security issues related to information technology. You may be evaluating elements of a single IT asset, such as a website, or performing a vulnerability assessment for an entire organization by looking at risks to a network, a server, a firewall, or specific data sets. List potential threats (such as hackers, former employees, or other unauthorized users) and vulnerabilities (such as insufficient passwords, software bugs, and employee access to sensitive data). After assessing risk and impact levels, assign a priority status to each entry, and create plans for resolving the issues. This is a spreadsheet-style template that you can easily customize based on the type of business and IT system.
Download IT Vulnerability Assessment Template
Patch and Vulnerability Management Plan Template
This vulnerability management process template provides a basic outline for creating your own comprehensive plan. Documenting procedures for patch management is a vital part of ensuring cybersecurity: By creating a patch and vulnerability management plan, organizations can help ensure that IT systems are not compromised. The template includes sections for describing the scope of the management plan, roles and responsibilities involved, policies to be followed, methods for ranking risk, and remediation steps. You may also want to include an inventory of specific system components or other information based on your business needs.
Download Patch and Vulnerability Management Plan Template
Excel | Word | PDF | Smartsheet
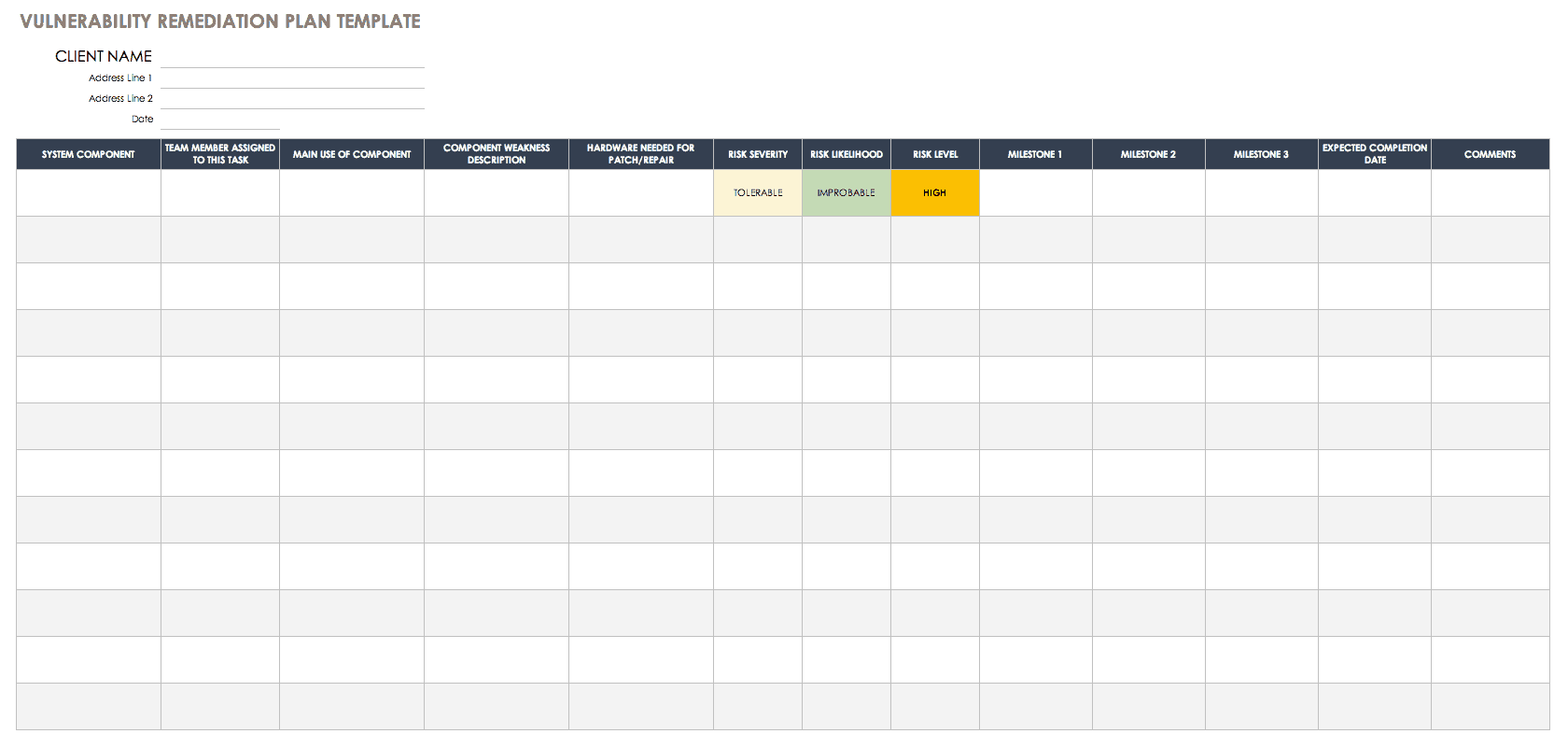
Vulnerability Remediation Plan Template
Create a vulnerability assessment action plan template that focuses on remediation. List weaknesses to be addressed along with remediation plans, deadlines and milestones, risk levels, and status updates. This template is available in Excel or Google Sheets formats and can be modified for a variety of assessment and planning uses, whether you’re dealing with security for a facility, information technology, or another system.
Download Vulnerability Remediation Plan Template
Excel | Google Sheets | Smartsheet
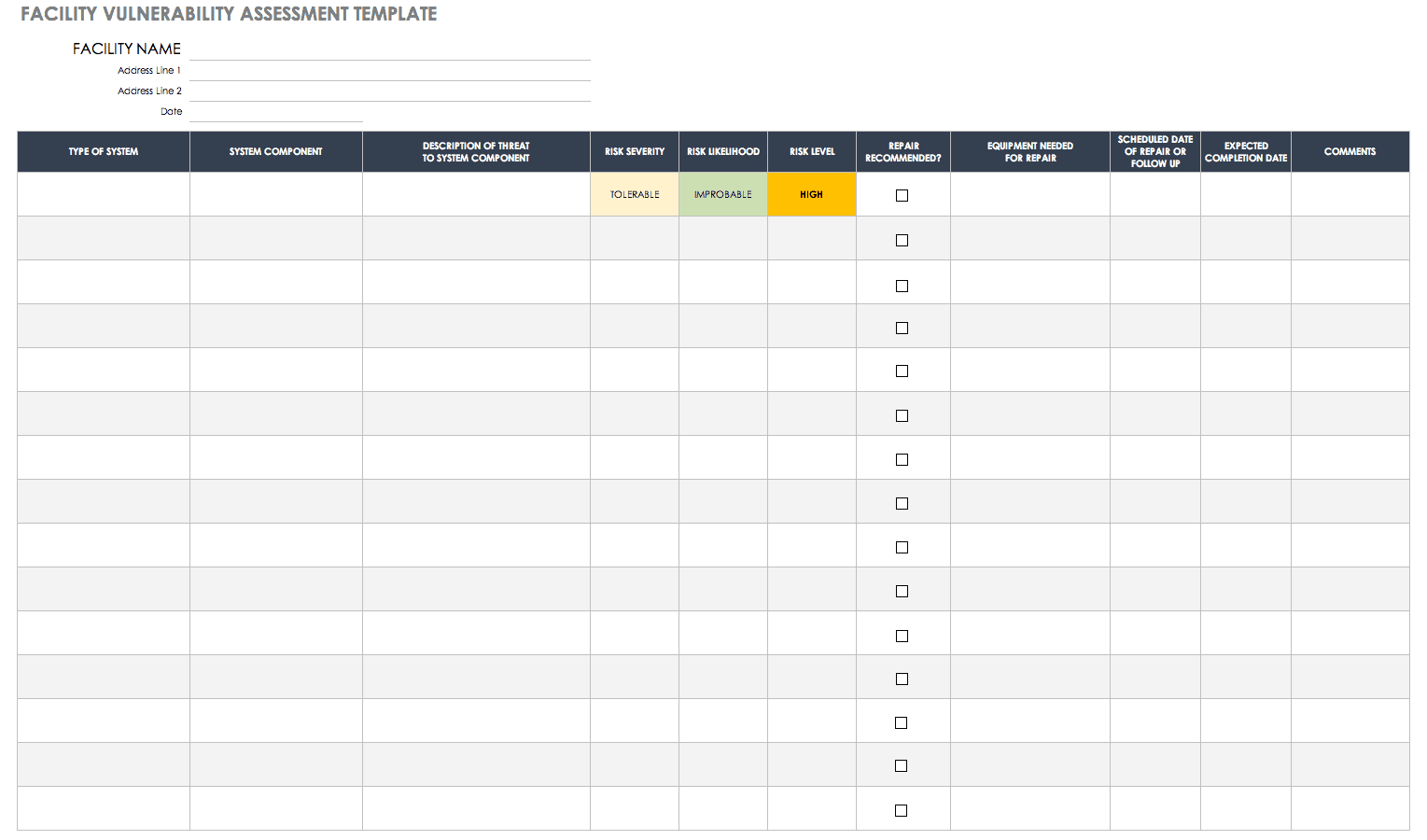
Facility Vulnerability Assessment Template
This simple assessment template allows you to list the critical parts of a facility so that you can quickly see which assets are the top priority when it comes to evaluating vulnerability. Identifying these important components can also inform your understanding of potential threats. The template is designed to help you assess risk based on the likelihood of threats occurring, the severity of the impact those threats might have, and the effectiveness of a facility’s current security or safety measures.
Download Facility Vulnerability Assessment Template
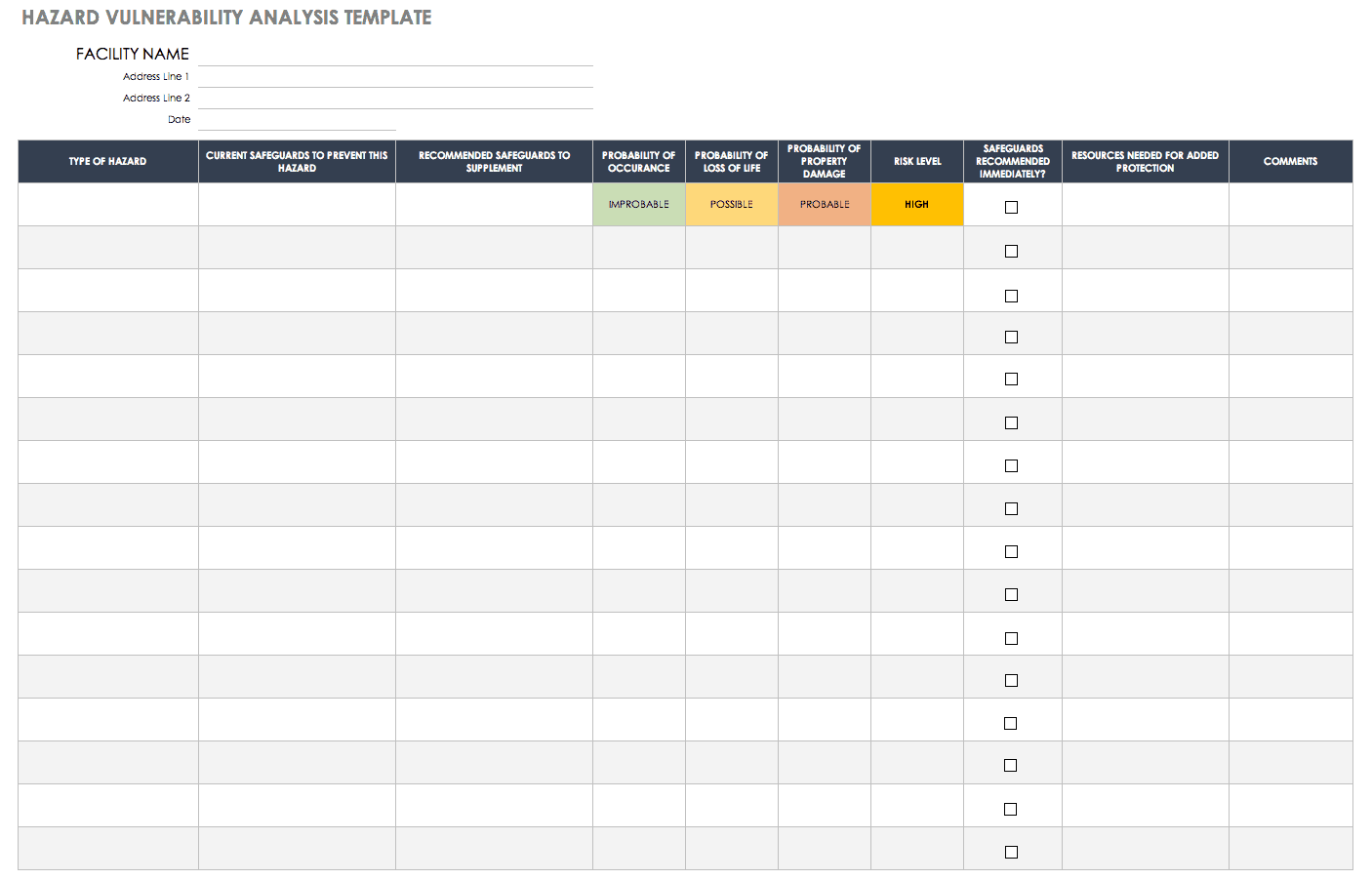
Hazard Vulnerability Analysis Template
The range of possible hazards is enormous, but most businesses could be negatively impacted by threats such as a natural disaster, a power outage, a fire, or criminal activities like a robbery or a data breach. No matter what hazards you are concerned about, this template can help you to prioritize and prepare for them. Identify probability, impact, and current level of preparedness to determine how to respond. You can even prepare for drastic events or dangerous hazards to minimize impact.
Download Hazard Vulnerability Analysis Template
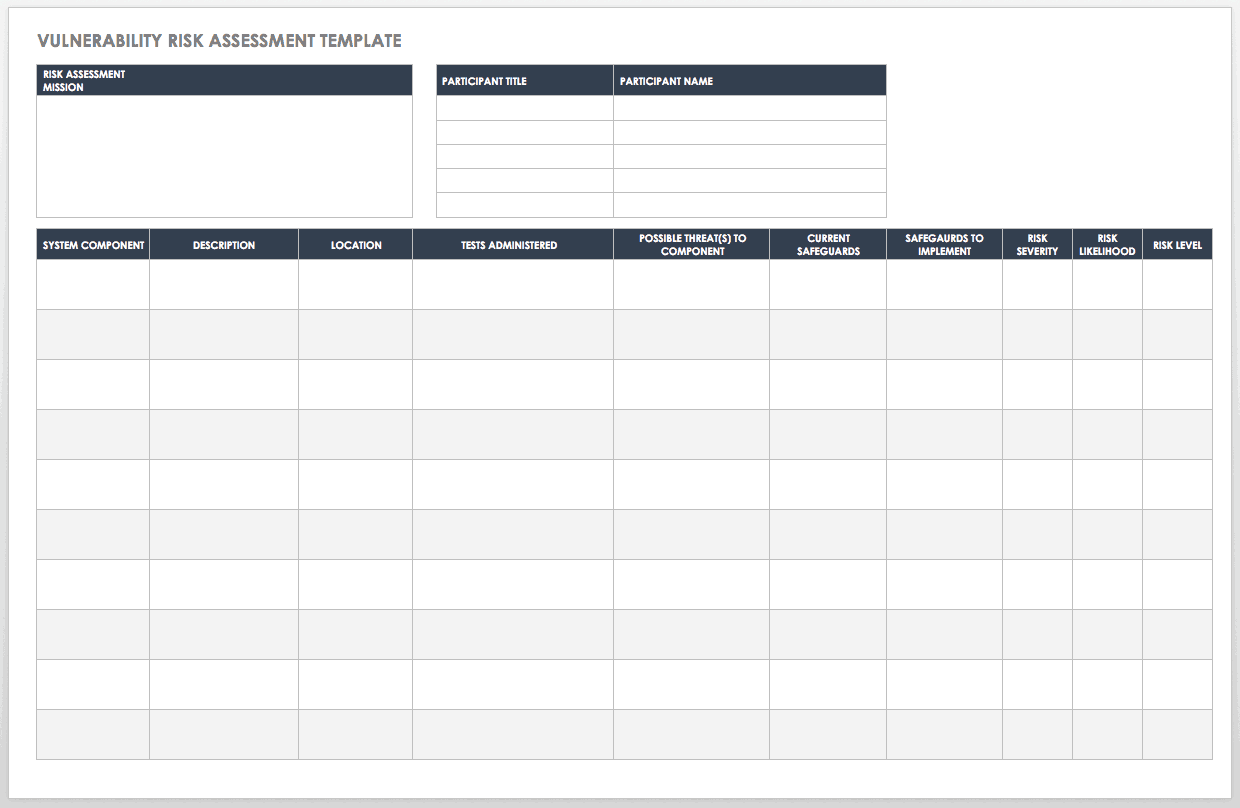
Vulnerability Risk Assessment Template
Use this outline to create a thorough vulnerability risk assessment report. Available as a Word document or fillable PDF file, the template provides sections for an introduction, the scope of the risk assessment, methodology and key roles, a breakdown of the system being assessed, vulnerabilities and threats, and recommendations. Compile your risk assessment information into an easy-to-read format with the included tables.
Download Vulnerability Risk Assessment Template
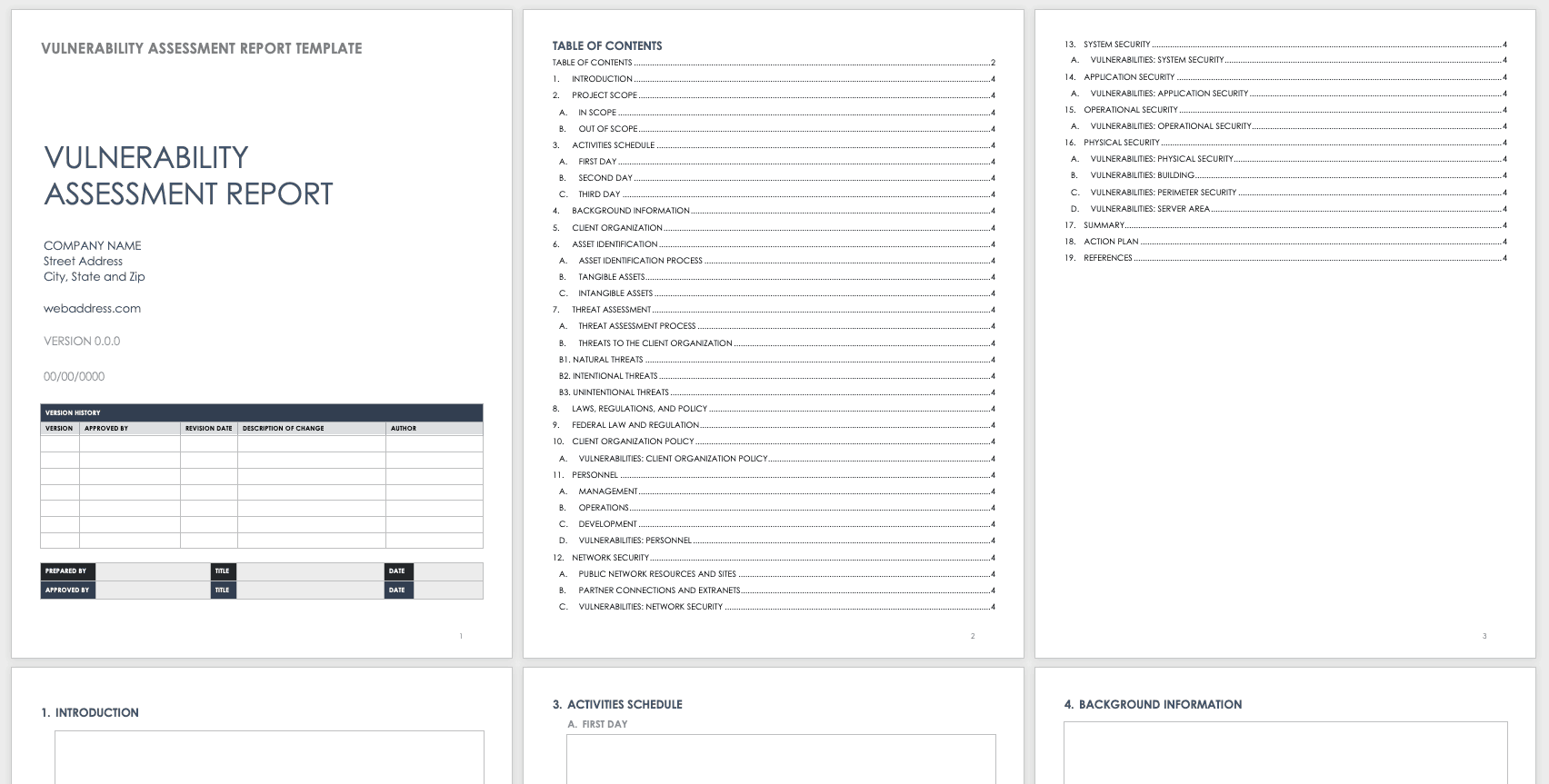
Vulnerability Assessment Report Template
Designed for assessing an entire organization, this security vulnerability report template is structured as a comprehensive outline. Depending on the needs of your business, this assessment report may touch on threats and vulnerabilities related to personnel, operations, buildings and other facilities, IT security, and other factors. You may need to include information on laws and regulations as they pertain to security policies. The template includes space for an action plan to address the identified vulnerabilities.
Download Vulnerability Assessment Report Template
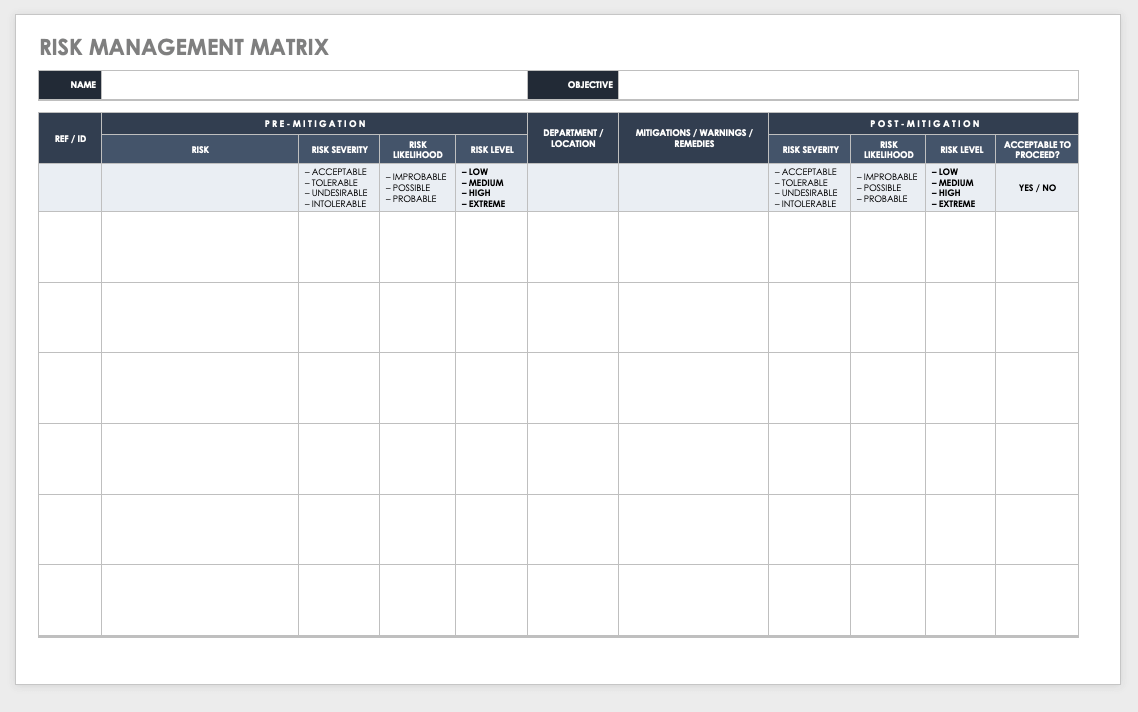
Risk Management Matrix Template
A risk matrix is a quick tool for evaluating and ranking risk. This template combines a matrix with management planning and tracking. You can assess risk levels before and after mitigation efforts in order to make recommendations and determine when a risk has been adequately addressed. This is a simple way of organizing and evaluating risk for any organization.
Download Risk Management Matrix Template
Smartsheet | Excel | Word | PDF
Threat, Vulnerability, and Risk: A Closer Look at Assessments
From financial losses to tarnished reputations, companies face major consequences if their security is compromised. This is why vulnerability assessments are so important: They enable organizations to examine and address vulnerabilities in a given system before they become problematic. Because businesses grow and technologies change, doing assessments on a regular basis is also critical for staying on top of emerging threats. Here are some definitions to keep in mind when undertaking an assessment:
-
Vulnerability: This is a weakness in a system that could lead to a breach in security or other negative impact if exploited (intentionally, accidentally, or by chance, such as with a natural disaster).
-
Threat: An event or condition that could cause harm or otherwise have an adverse effect on an asset. Threats can be intentional acts, such as hackers stealing credit card information, an accidental occurrence, or an environmental event.
-
Impact: This addresses the ways in which a system may be affected by a threat, and the severity of those effects.
-
Risk: The potential for a threat to exercise a vulnerability, leading to a resulting impact. The level of risk may be low, medium, or high depending on the likelihood of a threat occurring, the seriousness of the impact, and what controls are in place to prevent or reduce risk.
A vulnerability assessment generally examines potential threats, system vulnerabilities, and impact to determine the top weaknesses that need to be addressed. Risk assessment is a separate but related endeavor that also examines probable threats and impacts in order to mitigate potential issues. To learn more about risk management and find associated templates, read these articles on risk management planning and project risk management. You can also get tips on using a risk matrix to accurately classify risks as low, medium, high, or extreme.
Many organizations use vulnerability assessments, from hospitals to corporations to government facilities, such as water supply systems. A business may need to examine vulnerabilities related to a building or other structure, former and current personnel, cybersecurity, and more. Whether you’re evaluating a facility or software, performing regular vulnerability assessments can help you plan for future upgrades, get an overall picture of security health, prioritize specific issues, and ensure that you get the most from your security investments. While there are differences when assessing a building versus internet security, the basic steps in vulnerability assessment and management include the following:
-
Threat Assessment: This is the process of identifying potential threats and actions that could take place. As mentioned above, a threat can vary from a hacker to an inadequately trained employee to a terrorist or a natural disaster. Examples of threatening actions that could occur (depending on the type and location of an organization) include data theft, a terrorist attack, fraud, flooding, or a tornado.
-
Vulnerability Assessment: After determining threats, identify weaknesses, which are vulnerabilities that increase the chance of a threat event impacting a system or asset. Like threats, vulnerabilities will vary depending on the type of system and its complexity. Some examples include not collecting employee IDs after terminations, inadequate protective equipment at a facility, firewall issues, and inadequate staff training. If, for instance, an employee ID is still active after that person has been fired, the threat of a disgruntled employee accessing proprietary information becomes greater.
-
Rating Likelihood and Impact: Both threats and vulnerabilities are ranked based on a combination of probability and impact. An impact assessment looks at the degree of impact to an organization or asset if a vulnerability is exploited. The impact of a power outage could be a reduction in revenue, data loss, or even serious injury, depending on the type of business and work being performed. Likelihood and impact can be rated from high to low in order to quantify vulnerabilities and threats, and you can organize these ratings into an actionable plan.
-
Making Recommendations: After carrying out and analyzing an assessment, create a plan for addressing vulnerabilities. Some basic examples of action steps include implementing stronger passwords or retrofitting a building for increased safety.
-
Reevaluation: New threats and vulnerabilities may come up as others are being addressed. After implementing recommendations, it’s important to reassess a system on an ongoing basis.
Some organizations use third-party vendors to conduct assessments or implement security software to scan for IT vulnerabilities. No matter what method you choose, vulnerability assessments are important for both large and small organizations.
Improve Security and Safety with Vulnerability Assessment Templates from Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.