What Is Information Security Management (ISM)?
Information is an important asset and, as such, an integral resource for business continuity and growth. Information security management (ISM) sets the controls that protect confidential, sensitive, and personal information from damage, theft, or misuse.
Information comes in many forms, requires varying degrees of risk, and demands disparate methods of protection. You manage information assets differently based on the potential damage from threats and vulnerabilities. You must factor both human and behavioral elements into these controls, as well as the technology you’ve implemented to thwart attacks, breaches, and misuse.
Why Is Information Security Management Important?
Information security is a hot topic. Proprietary, confidential, sensitive, and intellectual data or information are all recognized as valuable assets that require protection from internal and external threats. If information is breached, stolen, or mishandled, it can cause personal harm to an individual, impede the ability for a business to continue operating, tarnish a reputation, and result in extensive financial damages, including reparations and regulatory fines.
Information security management helps organizations stay on top of threats and vulnerabilities, minimize and mitigate risk, and ensure business continuity. With the rise in cybersecurity risks, information security management has become even more important. Many industries have mandated information storage, usage, transmission, and disposal compliance requirements that are monitored by government and/or industry regulators.
By formulating management policies and plans, organizations can take the first step in developing an information security management system. These systems also require continuous updates and improvements to meet the organizational, managerial, and technical demands that keep information safe from accidental or intentional disclosure.
Who Is Involved in Information Security Management?
Information security is no longer just a set of directives and equipment that is managed by the IT department. It is now a top-down initiative that spans multiple operational areas, including the C-suite, human resources, finance, sales, and customer service, as well as IT.
ISM sets the goals and provides oversight for the development of ISMS that controls the integrity, accessibility, and protection of sensitive information. For example, employees may accidentally encounter or steal internal information without external interference. As such, organizations need to develop a culture that stresses the importance of information security. ISM provides both technological safeguards and policies that set guidelines and educate about confidentiality. With ISM, the organization can define and deploy the process so that employees don’t mishandle information.
Information Security Management Across Industries
All organizations that maintain sensitive or confidential data need an information security policy and plan, whether it’s detailed in two pages or 200. Employee records, which include Social Security numbers and other sensitive personal data, are an example of information assets. Organizations typically maintain these in a file cabinet or in the cloud.
However, several industries have regulations that carry compliance reporting responsibilities. Financial institutions and banks fall under the Payment Card Industry Data Security Standard (PCI-DSS), federal agencies follow the Federal Information Security Modernization Act (FISMA), and the healthcare industry adheres to information protections and compliance functions under the Health Insurance Portability and Accountability Act (HIPAA).
What Is the Federal Information Security Management Act?
The E-Government Act of 2002 addressed information security for government data and protection. That mandate became the Federal Information Security Management Act (FISMA). FISMA called for the development, documentation, and implementation of a “risk-based policy for cost-effective security” for all federal agencies. It also mandates yearly reviews of information security to prove the risk of a breach is at or below accepted standards.
Federal agencies work with the National Institute of Standards and Technology (NIST) to achieve and demonstrate compliance. NIST is charged with developing standards and a validation process framework for agency information security. The compliance framework calls for information asset inventory, risk assessments, security controls and plans, certifications, and monitoring.
In 2014, the Federal Information Security Modernization Act, also known as FISMA reform, was signed into law. The new mandate emphasizes information asset protection and response to cybersecurity risk.
What Does ISMS Stand For?
Information security management systems (ISMS) are made up of controls, processes, plans, and policies that are continually updated as security needs change. The purpose of an ISMS is to outline the security goals, management, and mitigation plans for information assets.
An ISMS is not one-size-fits-all structure, but is built with organizational need, risk assessment, and known vulnerabilities in mind. Business size, industry regulations and security requirements, processes, and overall objectives also factor into the development of the ISMS. The ISMS provides a level of risk assurance based on process maturity and broadness of implementation. An independent audit by a certification body CB can approve an organization's ISMS.
What Are Information Security Policies?
According to Michael E. Whitman and Herbert J. Mattord in their book Management of Information Security, “a quality information security program begins and ends with policy.” A policy is a high-level set of rules that drives decision making. An information security policy, such as one for large enterprises, is sponsored by executive management and written in a short, to-the-point manner. The policy should consider the culture of the organization and its risk factors, and should also recognize outside influences, such as the regulatory environment.
Internally, the policy should have an owner who is responsible for oversight, implementation, and continuous improvement. This includes setting realistic goals, identifying organizational weaknesses, and communicating version implementation so that the most current policy is always in use. For example, a policy may state, “We will monitor and/or block all internet sites that are deemed harmful or unrelated to business.”
What Is an Information Security Management Plan?
The information security management plan includes tactical details on how you intend to achieve the policy. Since information security is more than the purchase and use of technology to protect the data, Whitman and Mattord state that, in order to succeed, a plan must have the cooperation and buy-in of everyone involved. Using a framework such as the NIST model or ISO 27001, an information security management plan defines and implements controls that focus on running the information system, security methods, and technical controls associated with the technology solutions.
An information security management plan typically includes management, operational, and technical safeguards. Below you will find a sample list of security controls that can be included in your security management plan:
Management:
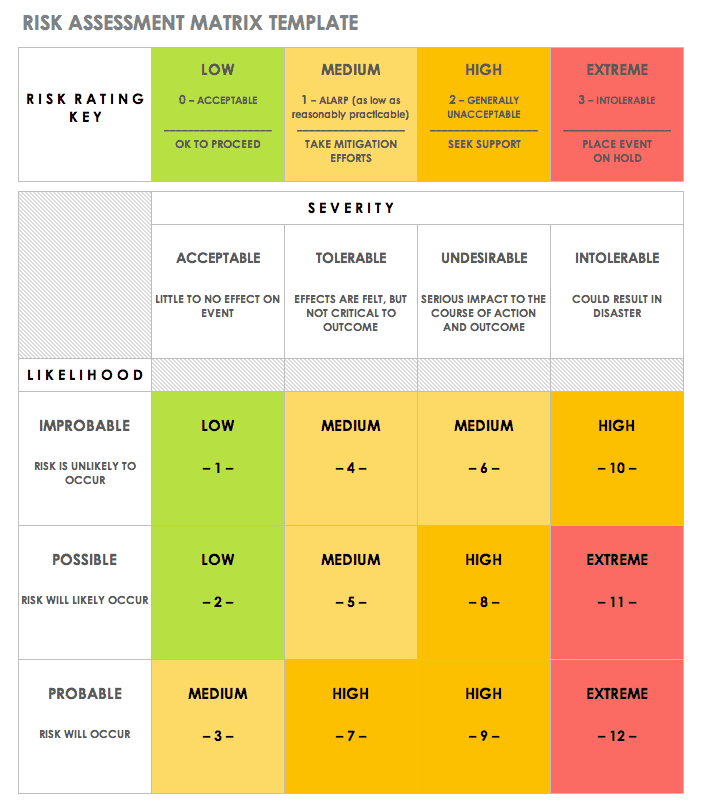
- Risk assessment
Download Risk Assessment Matrix Template
Excel | Word | PDF | Smartsheet
- Planning
- System and services acquisition
- Certification, accreditation, and security assessments
Operational:
- Personnel security
- Physical and environmental protection
- Contingency planning
- Configuration management
- Maintenance
- System and information integrity
- Media protection
- Incident response
- Awareness and training
Technical:
- Identification and authentication
- Access control
- Audit and accountability
- System and communications protection
A data security plan is an essential part of your overall ISMS. Below you will find a template that will help you plan for data security and guide you in the development of other information security plans.
What Is the Information Security Management Framework?
The International Standards Organization (ISO) develops standards and frameworks spanning all industry verticals, including manufacturing, food safety, technology, and healthcare. ISO/IEC 27001 is one of over 20,000 standards created by ISO. ISO/IEC 27001:2013 focuses on the structure and implementation of an ISMS.
What Is ISO/IEC 27001?
The International Standards Organization 27001 (ISO/IEC 27001) standard “specifies the requirements for establishing, implementing, maintaining, and continuous improvement for an information security management system.” The flexible framework is structured so that organizations of all sizes can implement it. Like the NIST framework for federal agencies, ISO/IEC 27001 is a best practice framework to guide the development of an ISMS. The standard is updated regularly, and includes 114 security measures organized in 14 control clauses.
These clauses are listed below:
- Clause 5: Information Security Policies
- Clause 6: Organization of Information Security
- Clause 7: Human Resource Security
- Clause 8: Asset Management
- Clause 9: Access Control
- Clause 10: Cryptography
- Clause 11: Physical and Environmental Security
- Clause 12: Operations Security
- Clause 13: Communication Security
- Clause 14: System Acquisition, Development, and Maintenance
- Clause 15: Supplier Relationships
- Clause 16: Information Security Incident Management
- Clause 17: Information Security Aspects of Business Continuity Management
- Clause 18: Compliance
The 2013 standard places less emphasis on the long-standing practice of plan, do, check, act (PDCA), also known as the Deming Cycle. (William Edwards Deming is credited with modern quality control initiatives, including PDCA, total quality management, and plan, do, study, act.) Instead, the standard focuses more on measurement and evaluation against organizational goals.
The standard also includes guidance for compliance when organizations outsource all or part of their IT or ISMS to a third party.
An accredited organization can certify ISMS as ISO 27001 compliant. The certification is a multistage audit performed by a third party.
The Benefits of an ISMS: Why You Need One
It is easy to understand why even small organizations require an ISMS. Maintaining information integrity is both a function of how an organization secures sensitive information and how it plans for mitigating threats as they increase in scope and frequency.
Today's information integrity cannot wholly rely on technology solutions and firewalls. Internal misuse can be as damaging as a technical breach. Thus, organizations must educate the workforce on the proper handling of sensitive and confidential information. A top-down ISMS recognizes and plans for information protection by physically sheltering assets, as well as preventing misuse internally, whether by accident or design.
An ISMS will defend against information breach or misuse, but if a breach occurs, it will also provide plans to minimize damage. When an organization applies a regulatory framework, it helps prove that its systems are in compliance in case of an audit. You can construct an ISMS to factor multiple regulatory mandates into one cohesive structure that is visible to all stakeholders.
Preventing breaches or misuse of sensitive or confidential information engenders trust, which is a market differentiator for many industries. And by having a structured system that values both policy and technology modernization, you institutionalize continuous improvement, budgets, documentation, monitoring, long-range forecasts, and education within the corporate culture for information integrity and availability.
How to Implement an Information Security Management System
People, process, and technology are essential for the successful implementation of an ISMS. When implementing an ISMS, you’ll notice many similarities to a change initiative. First, you generate buy-in from all stakeholders. You can best accomplish this through informing, training, and developing a culture of information protection.
Many organizations institute a PDCA protocol. This model establishes a cyclical and repeatable process for initiating, analyzing, and updating the ISMS. The goal is to practice continuous improvement as information security protocols evolve to meet the changing threats and regulations.
- Plan: Gain buy-in from stakeholders, analyze security needs, establish the ISMS policy, objectives, processes, and procedures.
- Do: Implement the ISMS policy and train personnel.
- Check: Analyze and monitor the performance (performance testing) of ISMS processes against milestones and measure overall effectiveness.
- Act: Continually correct and improve the ISMS.
What to Look for in Information Security Management Technology
With technology solutions, you can build and implement an ISMS more easily than you could adapt a system from a one-size-fits-all generic model. Many solutions include databases with controls for common threats and vulnerabilities. Reporting is an important feature that is more functional if templates are customizable while still aligning with ISO 27001 or other frameworks.
Look for a system that can meet the organization's unique needs for regulatory or legislative reporting, accessibility controls, and integrations with third-party partners.
Features to look for:
- Standards Compatibility: Ensure the solution aligns with ISO/IEC 27000 and other important ISMS policies and standards.
- ISMS Evaluations: Look for the ability to support risk assessments (ethical hacking) and other periodic process and security assessments.
- Activity Tracking: Monitor and track audits, security incidents, infrastructure changes, and security measures.
- Relationship Building: Map relationships between assets, such as information systems, processes, and services.
- Reports and Dashboards: Create reports and dashboards, including a risk register, that are relevant to various stakeholders.
As cybercrimes increase, the need for information security is a top priority for many CEOs —and it can provide a competitive edge. Organizations that successfully protect valuable and vulnerable information enjoy the benefits of industry leadership and regulatory compliance, as well as maintain the trust of their customers. Implementing an ISMS isn’t always easy, and it requires buy-in from the organization, but the benefits are worth the investment in the long run.
Improve Information and Data Security with Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.