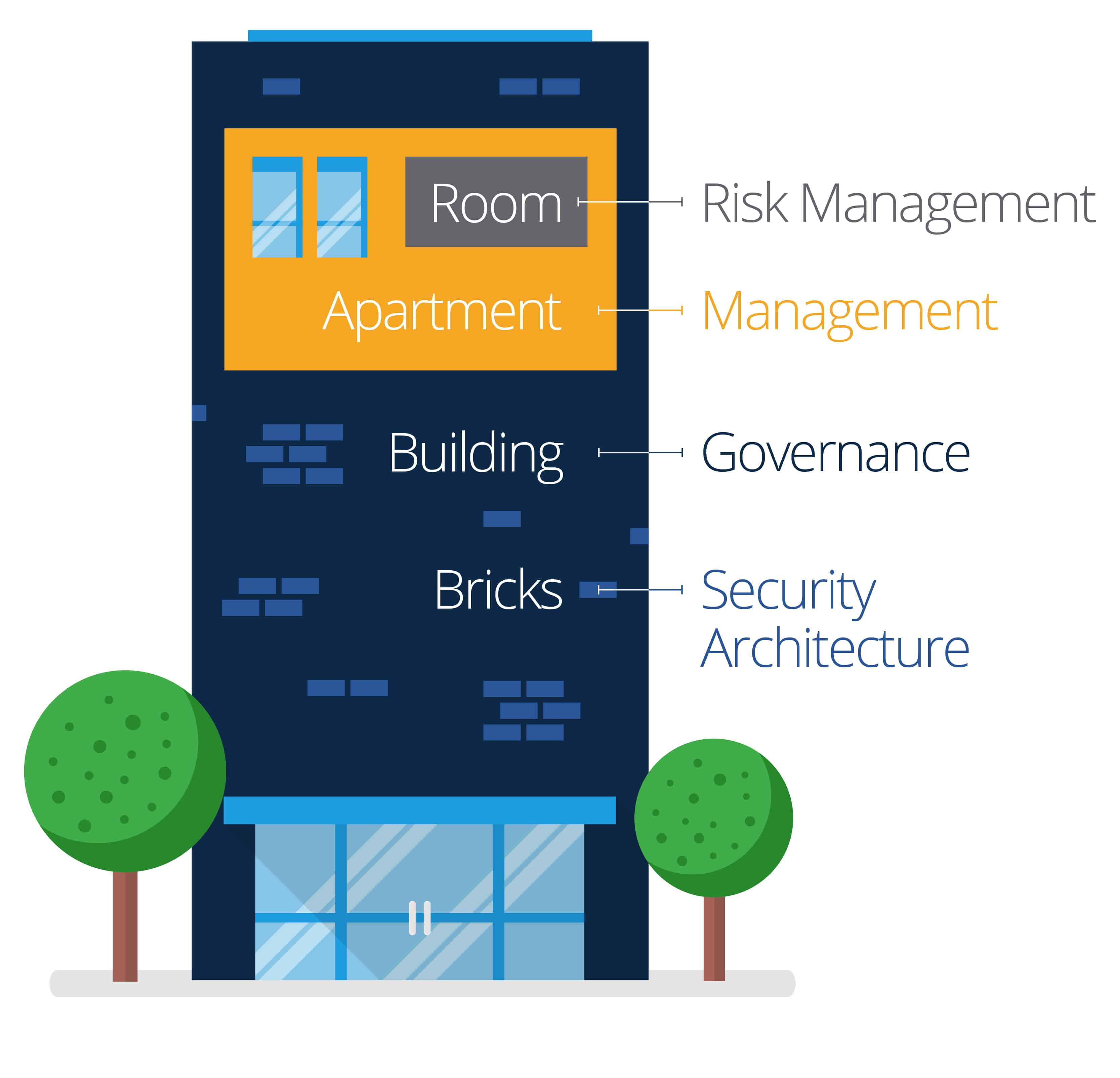
What Is Meant by Enterprise Security?
Enterprise security includes the strategies, processes, and infrastructure needed to protect the physical and digital property of an enterprise.
What Is Enterprise Security Management?
Enterprise security management (ESM) is a systematic and integrated process for addressing concerns about unauthorized access through policy and judicious configuration of assets and security tools. ESM considers all risks that may impede or damage the essential and critical functions of an organization. As a holistic endeavor, enterprise security management applies security policies across the organization, including multiple platforms, infrastructure, and all security point products, devices, applications, and business processes. Enterprise security also encompasses regulatory compliance and applies compliance frameworks for guidance.
Enterprise security includes not only the assets and data that are stored and manipulated on site, but also transactions and information that reside on or pass through distributed devices, private employee devices, and the cloud. It reaches beyond physical and information security, and concerns internal and external threats, and intentional and unintended problems caused by employees.
Enterprise security management efforts are led by enterprise leadership teams, including (but not limited to) the CIO, CISO, and CSO, who encourage a security-minded culture. They also promote security as a strategic endeavour.
What Is Enterprise Security Governance?
Enterprise security management may be considered an expression of enterprise security governance. Enterprise security governance is like a roadmap for determining a strategic plan to fulfill regulatory and other requirements, control risk, and appropriately manage human and financial resources. Governance requires that management sponsors the efforts to ensure that mission and vision align with business goals and compliance obligations.
Some of the recognized governance frameworks for enterprise security include the following:
- COBIT (Control Objectives for Information and Related Technologies): Best practices for aligning technology and business requirements.
- ITIL (formerly known as the Information Technology Infrastructure Library): A set of best practices for aligning IT services with business requirements.
- ISO 27001 (International Organization for Standardization): Includes requirements for information security management.
- NIST (National Institute of Standards and Technology): NIST provides at least one framework for cybersecurity.
- HIPAA (Health Insurance Portability and Accountability Act): A federal law that protects the privacy of individuals and their health records.
- PCI DSS (Payment Card Industry Data Security Standard): A set of best practices created by the industry to protect personal information during debit and credit card and other electronic transactions.
- SOX (Sarbanes Oxley Act): A federal law governing corporate financial reporting.
- FISMA (Federal Information Security Management Act): The framework for protecting government information against natural or man-made threats.
- GLBA (Gramm-Leach-Bliley Act): A federal law that restricts how financial institutions manage individuals’ private information.
For more information, see our article on Understanding IT Compliance.
What Is Enterprise Security Risk Management (ESRM)?
If enterprise security management provides the organizational structure and culture for enacting security plans, enterprise security risk management is the process of identifying risks and threats, determining how to mitigate them, and documenting policies and best practices to proactively and reactively address future occurrences.
Components of ESRM
You can approach ESRM like a project with its own vision, mission, and goals. The vision is to protect the assets of an entire organization so that it can execute its larger business vision and mission. The mission continually identifies, analyzes, and responds to risks to the business. The goals create, maintain, and promote policies and best practices to protect the organization against security risks.
How to Implement Enterprise Security Risk Management
Although specific applications of ESRM may differ, the following are generally accepted steps to managing risk:
- Survey Assets Organization-Wide: To understand what’s at risk, you must know what assets and critical infrastructure and resources you have, and why they are important.
- Threat Modelling and Assessment and Risk Assessment: Take an honest look at the current security of your enterprise. What are your vulnerabilities and what are the risks to each asset? Who are your competitors? Who else might want to impede your business? Some basic risks to consider include the requirement for SSL and authorization checks, and measures against SQL injection.
- Develop Plans for Risk Mitigation: Coordinate with the stakeholders to determine how to manage risks and identify security objectives. Options include stopping risky activities, planning mitigation for security events, or simply accepting the risk.
- Create a Corporate Security Policy: Creating a corporate security policy is essential, and must cover all aspects and assets of the organization.
- Pursue Continuous Improvement: An enterprise security effort may start as a discrete project but requires ongoing consideration. Those charged with security must keep current with threats and trends within the organization and beyond. Security incidents require proper root cause analysis — this should include team members beyond those directly charged with security. Incidents represent obvious opportunities to reassess risks and responses, and threat analysis and response plans should be reviewed regularly, regardless of whether an incident has occurred.
Security Policy
Without question, your security policy must apply to the entire organization. Parts of the policy may include the following:
- Network Access Guidelines: Who is allowed access to the network? What parts are restricted? Are there time restrictions on usage?
- Password Guidelines: What forms a strong password (for example: length and complexity)? How often must it be changed?
- Network Usage: What is acceptable and unacceptable use of the network?
- Mobile Device Policy: What devices may be used on the network, and what data or programs may they access?
- Physical Controls Policy: Do you control access to server rooms? Do you store backups in secure locations? What’s the strategy for protecting physical access?
- Policy Enforcement: What are the consequences, if any, if policies are violated?
Your policies may include checklists and report templates, such as the information security incident report template found here.
Common Organizational Behaviors That Limit Security
Fifteen years ago you might have assumed that computers with a powered-down modem and an office with a locked front door would sufficiently protect your network and data. That is no longer the case. Rather, today’s security must be strategic, systematic, and repeatable. The following are common ways that organizations sabotage their own security.
- Thinking of security as a standalone practice. Enterprise security can’t be siloed. It must be integrated into the core competencies of your organization and involve every team member.
- Failing to patch and upgrade out of fear of disrupting the flow of work. Staying on top of upgrades and patches is one of the simplest and most effective ways to protect your network. Patches should receive a higher operational priority.
- Unfettered BYOD (bring your own device).
- Casual attitudes to security. Leaving backup devices unsecured on filing cabinets or in cubicles, and the lack of screensaver passwords to secure laptops and desktops when unattended.
- Assuming that endpoint security and passive scans suffice. The prevalence of web applications makes almost every site vulnerable to cross-site request forgeries, XSS cross site scripting, and more. Sites require robust security such as OWASP technology. Networks must be proactive, constantly monitoring for threats and understanding new risks.
- Testing while software deployments are in staging, but no ongoing testing once the system is live. Mirroring, where two copies of a database sit on separate computers, works for testing, and doesn’t disrupt work or customer access.
- Viewing security as a one-time project. Vulnerability analysis and threat monitoring must be constant. Security now must be proactive as well as reactive.
- Not setting up a separate network for guests and wifi. Separate networks can help isolate malware and protect sensitive data from unauthorized access.
Enterprise Information Security Management
Enterprise Information Security covers CIA: the confidentiality, integrity, and accessibility of information. But it also covers compliance. For information security management purposes, information can exist in structured sources like databases, or unstructured sources, such as Word docs, images, and PDFs. The practice of enterprise information security includes understanding who should have access to what information. Enterprise information security now relies on Identity and Access Management techniques to secure data.
What Is Security Architecture?
Security architecture describes the overarching design for implementing security infrastructure in relation to the rest of the system’s architecture. These controls are in place to maintain the confidentiality, integrity, and availability within the system (these are called quality attributes). Strong security principals may include separate security domains, or use trust levels and tiered networks, and include the means to ensure the resilience of business functionality after security incidents. The architecture should also be based on recognized industry best practices and regulatory frameworks.
Avoiding Mobile Mayhem: Enterprise Mobility Security Best Practices
The personal PC revolution brought the power of the office workstation into the home. But now employees want to integrate their own tools and devices into the workplace. Besides laptops, devices include tablets and cell phones. This creates a myriad of possibilities for introducing malware into the network or losing data.
“For those larger organizations, mobile device management (MDM) tools can be an effective way to manage the range of mobile devices out there and ensure basic security hygiene — such as full disk encryption — is being enacted,” says Caudill.
Mobile Device Management (MDM) programs contain enterprise content in an encrypted space, separate from the user’s private content. Some programs may also prevent content within emails and attached documents from being copied to the user’s desktop or forwarded outside the organization's domain. MDMs often also provide secure browsers that can filter URLs. Other features include logging of VPN (virtual private networks) and other connections.
Two powerful and potentially controversial services of MDM include geolocation and geofencing. With geolocation, lost and missing devices can be tracked, allowing you to recover expensive assets and sensitive data. However, a side effect of geolocation is tracking employees. For example, companies can see if the device — and the employee carrying it — visits competitor sites. Similarly, geofencing can send alerts if a device is carried into a restricted area of the facility.
MDM programs employ server and client elements, which may be provided by your current third-party vendor or another. IT administrators manage all device users from a centralized console, which provides visibility and heightened security in mobile use.
Why Your Organization Needs an Enterprise Security Management Suite
Security today must be end-to-end and organizationally pervasive. But how can an IT or security team manage it all while still performing operational duties? Increasingly, organizations will need an enterprise security management platform. Functionality is usually controlled by software agents, who scan and manage from a central security service located on a server. ESM components often focus on user administration and vulnerability assessments, and include the following responsibilities:
- Manage security across programs and platforms.
- Enforce password and SSO (single sign-on) policy.
- Manage adding and removing temporary and terminated employees.
- Alert the organization to threats and breaches.
- Bridge gaps between business processes and compliance requirements.
- Offer security reporting capabilities.
Benefits of Managed Security Service Providers (MSSP)
No matter how current and robust your IT team is, ESM software may be difficult to configure, let alone manage. You may find it advantageous to delegate network security to managed security service providers. Ensure that the offerings of any platform match your organization’s use cases, and look for these features:
- 24/7 monitoring and management.
- Timely detection of threats and breaches.
- Protection against malware, including Trojans, adware, spyware, spamming, phishing, and viruses.
- Ability to identity and access management solutions.
- Managed firewall and VPN solutions and end-point security solutions.
- E-mail security management and web security management.
What Is SIEM?
SIEM is the acronym for security information and event management. SIEM software offers a console-based view into networks, access, endpoints, and vulnerabilities, and provides real-time monitoring and threat event mitigation. A SIEM system searches logs, or information, to create reports on network, user, and application behavior, which it uses for analysis purposes to detect security events, and for compliance audits. SIEM systems may include or work alongside other security support approaches, including the following:
- Log management, to provide insight into system access and events
- Anomaly detection
- Incident forensics
- Configuration management, to ensure solid, repeatable build practices and to keep a historical record of how and when components were added
- Vulnerability management, to routinely identify and remediate system vulnerabilities
- Network flow analysis
- Threat detection and ability to monitor from network, servers, users, and applications
- Detection of high risk behaviors from billions of data points
- Analysis of behaviors in real-time or close to it
SIEM platforms may be implemented on premises and managed by an enterprise’s own IT security team, or purchased as a managed security service provider (MSSP), which also offers a dedicated staff to monitor, update, and maintain the service.
How to Pick the Best SIEM and Security Management Suite for Your Enterprise
As with any software investment, picking a security management suite should not be done hastily. Take the time to define your use case and consider the following factors before you buy:
- Do you have the knowledge and staffing necessary to customize your dashboards, connect to appropriate logs, and update your configuration as your network changes? No platform can perform all of the customization you want as-packaged.
- Determine whether your potential security suite can view events in the logs you want to monitor. In software, standard formats are not guaranteed.
- Ensure that your license selection is robust enough to cover all your devices and all potential events. You don’t want the program to suddenly stop logging after it reaches its limit.
- Verify that you can search across networks and devices and configure analysis rules as needed. Correlation engines, which scan for anomalies and policy violations, can be quite sensitive.
- Consider the usability of the product. If you can’t easily create reports, your remediation time in a security event may be hampered.
- Ask about support plans - 24/7 telephone support is usually standard, but some plans may also offer annual onsite visits.
Enterprise Security Management: The Bottom Line
Many terms exist to describe aspects of enterprise security management. Enterprise security can have an architecture, be based on a recognized framework, or focus on risks and remediation, and be automated through a security platform. To gain a deeper understanding of information security, IT professionals and others may consider a Global Information Assurance Certification or GIAC certification. But the essential takeaway is that a modern organization must view security as something that applies to every data source, every device, and every team member. It’s the only way to fortify enterprise security in today’s cybersecurity landscape.
Improve Information and Data Security with Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.