What Is an IT or Information Systems Audit?
For the IT professional, an audit focuses on current internal controls and their ability of to reduce the risk of harm to an organization or its stakeholders. The act of identifying areas of higher risk has emerged as a leading focus for audit departments. In the IT industry, confidentiality and data protection are the spheres of greatest vulnerability and regulation. However, the assessment of risks varies from industry to industry. The audit department is responsible for evaluating the current controls, deciding whether they are appropriate for the task, and determining what changes you can make to improve, achieve business goals, or meet regulatory compliance requirements.
What Is the Purpose/Objective of an IT Audit?
One conducts an information technology audit, or any audit, to identify areas of vulnerability and to recommend remedies to ensure protection. For the IT department, audits are a systematic examination of the policies, operations, and structure of the IT systems and infrastructure. These large mandates can cover an assortment of functional components that include security, data integrity, equipment, platforms, portals, and software. For example, a technology audit can focus on equipment, policies that factor into the governance structure, remote access, customer portal usage, and even business usage of social media.
An integral part of the overall audit is to evaluate how IT controls are functioning, the efficiencies of the controls, whether IT is meeting objectives, and whether functions fall within the specification of regulations and applicable laws. The results are boundless: An audit can clarify the need for a new technical capability that was previously unknown or required validation, and can also identify strong points that can become new products or services.
Various Types of IT Audits, including a Technology Audit
IT audits are not a one-size-fits-all proposition. An audit department can, on a regular basis, target areas of high risk for formal auditing. In fact, many audit departments conduct informal audits that take a snapshot view of a particular system. A technology audit of equipment for planning purposes may look very different from one that focuses on governance or social media activity. The areas for examination only continue to grow as technology progresses and businesses grow. Audits can be conducted for regulatory compliance, disaster recovery plans, mobile or remote access, software, management processes, and portfolio management — each will demand different sets of information, but they all require the same rigor and process. When formal, third-party audits occur, a common concern is the difficulty of determining which of the numerous IT functions the auditor might target. You can mitigate this concern by simply communicating directly with the auditors or regularly and proactively conducting self-assessments.
Audits go beyond IT to cover departments across organizations, including finance, operations, and administration. Additional potential types of audits include the following:
- Forensic audits
- Compliance audits (IT and non-IT)
- Technology innovation audits
- Systems usage/development and application audits (IT and non-IT systems)
- Facilities audits
- Enterprise communication audits (see below)
- Web presence audits (see below)
- IT and enterprise architecture audits
Web presence audits and enterprise communication audits are fairly new to the auditing industry. These types of audits evaluate whether all of the organization’s web presences and telephone communications are in compliance with company objectives and avoid compromising the firm’s reputation, leaking information, or putting the organization at risk of fraud.
The History of Auditing
The word audit has its roots in the Latin word auditio, which means a hearing. Audits became common practice as a way to protect partnership assets, such as those developed by large trading companies when they colonized the New World. The advent of computers added a new layer to the numerous auditable functions of an organization. The constant advances in technology and the need for both business and consumer-data privacy has expanded the use and purpose of auditing.
The IT Audit Process
Many organizations conduct audits across business departments on a regular basis. This, of course, includes the IT department. The development of an audit report begins with establishing a goal. During the audit, one gathers and reviews the evidence. If appropriate, you use computer-assisted audit technologies (CAAT) to facilitate the data evaluation process. Those conducting an audit expect the department under evaluation to cooperate with the process through interviews, easy access to information and data, and timely responses to questions. The auditor’s report should provide an unbiased and accurate account of any challenges they identify. The auditor should communicate their findings and conclusions in a timely manner, and supply clear and concise recommendations for corrective action as well as a timeline for additional review.
Here are the most common steps in the IT audit process:
- Establishing the audit objectives and goals
- Developing the audit plan in accordance with the objectives
- Gathering information
- Evaluating and analyzing data
- Providing audit findings
- Performing follow-up audits and actions and asking follow-up questions
Who Is Involved in the IT Audit Process?
IT audits occur in any industry that is responsible for protecting information, such as colleges and universities, banks, government departments, and most businesses. Large organizations often have internal auditors who work independently to conduct investigations, taking an objective look at policies, procedures, and technical controls that protect the company or stakeholders. Companies also use internal auditors to identify opportunities for greater efficiencies in business practices.
Many consider audits disruptive, which at times makes cooperation difficult to achieve. Many regard the auditing function as a waste of time or a painful process that is determined to find fault. However, when one conducts audits with a common goal, such as making a company stronger or more efficient, the process can facilitate cooperation and overall involvement. In order to ensure success and engagement, you should include employees from the IT department to the executive team, including the CEO, as well as suppliers. You can provide shareholders and customers of your enterprise with details of audit successes or with audit results that drive new initiatives.
IT Audit Standards and Controls
When an auditor conducts an IT audit, they pay special attention to evaluating appropriate controls. A control is a mechanism or policy that allows or restricts an activity. Common examples of controls are the number of password attempts allowed before a website will lock or time out. The control’s main function is to prevent activities that are harmful, such as releasing confidential information, under or overcharging a customer, or violating an industry regulation. Controls can be triggers, policies, or practices. They can be manual or automated processes.
As auditors perform audits, it’s important that they and management ensure that controls are effective enough to mitigate risk. It’s also crucial that they understand the true costs and benefits of controls (including how those controls impact the organization), keep the business purpose in mind and avoid altering that purpose with controls, and utilize an internal IT expert to fully understand specific system controls.
IT Audit Frameworks
IT frameworks are available to assist in the audit process. The National Institute for Standards and Technology (NIST) provides a valuable series of documents regarding auditing the IT system development lifecycle (SDLC). Of note is their 2014 framework for managing cybersecurity risk: NIST has structured this framework to help IT and audit professionals develop strategies and controls that align with the real risk tolerance of a business. The five actions that drive this framework are to identify, protect, detect, respond, and recover. It is what we call a multi-industry framework. Professionals also commonly employ industry-specific frameworks, such as HIPAA for healthcare and the Payment Card Industry Data Security Standard (PCI DSS) for financial institutions.
How to Plan for an IT Audit
Planning for an IT audit can be tricky given the broad array of IT activities. A systems audit is different than a forensic audit, just as an audit that focuses on user security differs from one that looks at governance. Auditors can conduct a formal audit process or take a less structured, informal look at a sampling of controls. A good method to prepare for an audit is to conduct regular self-assessments using methods, frameworks, or checklists provided by the company’s audit department. Another technique to proactively prepare for an audit is to invite key audit personnel to development meetings, so you can gain insight into what an auditor looks for when assessing controls for IT.
“Organizations should first make sure that their information security policy framework is complete, up to date, and approved. Security controls listed in the policies must also be in place and must operate effectively. These controls will depend primarily on the regulation or standard against which you are being audited. For instance, a bank or credit union may be audited against FFIEC regulations (under the GLBA), whereas a hospital system might be audited against the HIPAA security rule.
“Still, following industry-agnostic best practices is key when preparing for an audit. Consider access, management, recovery, and protection controls. Instate a user-education and awareness program, and remember to think about both physical security and cybersecurity. Use the Rivial Data Security IT Audit checklist to take inventory of processes in place for a basic technology stack and to assess other key components of a solid security program.”
IT Audits for Healthcare Organizations
Healthcare organizations are required to abide by stringent security measures and remain compliant with HIPAA guidelines, meaning regular audits are necessary to identify gaps in organizational processes and security and to accurately track who has access to protected health information (PHI), when secure data and information was accessed, and the reasons for access.
HIPAA regulations mandate that healthcare organizations implement procedures to regularly review and manage how information is stored and what resources have access to it. IT audits help to provide the visibility into this information, creating a system to accurately review historical security and operational activity, and improve the way information is stored.
Since healthcare companies must always remain compliant and regularly audit their processes and information access, they need a tool to help them keep track of changes in authorization, provide critical information for reviews, and ensure that the integrity of their systems is not in jeopardy.
Smartsheet is a work execution platform that enables healthcare companies to improve auditing processes and track and store auditable records in one centralized location, all while securely managing and sharing PHI under HIPAA’s regulatory requirements. Streamline reporting, organize all necessary information in one place, and set security and sharing settings to uphold data security standards.
Interested in learning more about how Smartsheet can help you maximize your efforts? Discover Smartsheet for Healthcare.
Why Do Companies Fail IT Audits?
There are numerous reasons a company or department may fail an audit. Remember that auditors can act as policing agents rather than partners. Just as often, those under audit believe that the process is a waste of time, so they are slow to implement audit recommendations. Both approaches can lead to an audit failure. Although there are other areas of difficulty for the auditor, such as gaining access to information or dealing with cumbersome manual processes and inadequate equipment inventory, you can combat most of these challenges by fostering a department culture that facilitates - rather than obstructs - the auditor’s work. You can train personnel to answer questions more effectively, implement automated functions or inventory for ease of retrieval, and take advantage of pre-audit self-assessment opportunities.
"During an audit audit, participants will incorrectly describe a control because they can’t understand how it applies to their specific job role. Another key reason for failed audits has to do with the disconnect between policies and other supporting documents, such as procedures, standards, and guidelines. These documents should serve to inform daily tasks and activities in a way that broader policies cannot. By failing to give real-world examples of how IT and business processes interrelate, users fail to ‘live out’ policies while performing their job duties.”
The goals of the independent auditors and the IT department should be in line with the overarching goals of the business. One of the easiest methods to achieve success is to simply treat auditing as a normal business function. Following are the most common reasons that organizations fail both internal and external IT audits:
- The IT team is unable to provide adequate information about technology assets.
- IT uses unreliable manual processes and decentralized tracking to provide audit data.
- IT has an inability or unwillingness to respond to change requests from the audit results.
- The staff and business are unprepared for the audit.
- Policies, procedures, and security controls (including security and patch updates for software and operating systems) are non-existent or outdated.
- Businesses lack disaster recovery and business continuity plans to prevent data loss.
- Businesses lack the tools to perform vulnerability tests.
- The IT staff is unable to provide a map of the network and/or infrastructure.
The aforementioned reasons for failure are the most common ones, but it is sometimes the case that IT auditors are challenged by rapidly changing and highly technical processes and equipment that make up a modern technology department. Auditors also have to consider the changing business environment, new risk elements that come with rapid advancements, privacy and data protection, regulatory compliance, and the complexities of new technologies and information delivery itself.
IT Audit Software Solutions
The purpose of employing a software solution for IT auditing is to provide collaborative opportunities through shared information that offers clarity to stakeholders. Reporting should focus on the fundamental needs and goals of the particular business or industry. Reporting and processes can include managing IT audit projects and reports, using risk analysis tools, making evaluations and recommendations, and tracking. The project planning elements can provide workflow calendars with information visible to both the auditor and those under audit.
Additional features and capabilities to look for in IT auditing software include the following:
- Web-based and mobile accessibility
- Internal controls management
- Risk assessment
- Compliance management
- Integrations for data collection
- Reporting and metrics
- Future planning capabilities
- Integration with an IT service management solution
How Is Technology Transforming the IT Audit Process?
The technology revolution continues to complicate and broaden the IT audit landscape, but the tools and technology now available also provide opportunities. Through automation and technology upgrades, large quantities of data analysis allow richer evaluations. Through the use of tools and technology, you can perform investigations more often and in a more timely manner for high-risk areas. The availability of big data, along with the use of cognitive technology or artificial intelligence, provides targeted analysis of large, diverse stores of information to assist in evaluations. However, technology advances are not the only transforming element — the technical knowledge and skills of the auditor are also changing. To move away from methods that provide only reasonable assurance, you may also call upon auditors to provide partnership rather than policing in their evaluations. The traditional audit role of finding something broken and recommending a fix is expanding into a more collaborative process that helps IT professionals develop the proper controls that provide the strongest risk remedies.
IT Audit Philosophies
An independent, unbiased, and unrestricted analysis is one of the main expectations of the auditing process. One achieves independence by separating the audit function from the general management function. While true independence is difficult to achieve, auditors can carefully examine the evidence for the purpose of protecting the company from the costs associated with harm. Auditors should use appropriate care in their investigations and present a fair and timely representation of findings. In addition to the findings, auditors may include supporting literature and documentation, innovation samples, scientific evidence, and proof of financial impact in their audit reports. Auditors should also act in an ethical manner to provide clear and unbiased reviews and recommendations. Factors that impede a company’s audit effectiveness include resistance to criticism and to making the necessary and recommended changes.
Risk Assessment and IT Audits
Because of the vast scope of IT functions, auditors tend to evaluate using a more risk-based approach. We use the process of risk assessment to identify and evaluate risks associated with a current or future activity. You can identify risk for an industry or company with the kind of information found in a business impact analysis (BIA).
You can also use risk assessments to identify what to audit. For example, identifying specific areas to be audited allows management to focus on those elements that pose the highest risk. Pinpointing areas for audit also allows executives to zero in on what’s critical to the overall business direction, allocate resources, and quickly maintain and collect relevant information. The audit assesses the internal controls in place to allow or prevent certain identified activities that pose a risk or threat. Just like the audits described earlier, an audit based on risk assessment strives to find and recommend remedies where one has detected vulnerabilities. Even within the scope of the audit, however, there are factors or practices that may not be adequately identified or risks that cannot be resolved. One example is the inherent risk in inadequate resource placement, such as a building that isn’t useful in its current location: An auditor may not be able to recommend a viable solution for this kind of challenge because relocating a building is not a simple (or viable) solution in most situations. Another factor is a residual risk, such as a data error that goes undetected even after a thorough audit process.
There are five main types of risks that are important to understand:
- Inherent Risk: The risk that there was a misstatement of fact or mistake in data gathering and analysis
- Control Risk: The risk that you will not detect or prevent this misstatement with internal controls
- Detection Risk: The risk that the auditor will not detect the misstatement
- Audit Risk: The risk that an auditor may make a mistake that you don’t detect
- Residual Risk: The risk that remains even after you implement and consider controls
IT Audit Certifications
IT auditing as a profession has an ever-expanding set of skills and requirements. A combination of on-the-job knowledge of IT functions and experience, strong analytical skills, and relevant certifications are now part of the requirements for good IT auditors. Industry organizations regularly introduce specialty areas of study as the IT audit scope broadens to include social media, virtual and cloud capabilities, and emerging technologies. Auditing certifications, such as the Certified Information System Auditor (CISA) and other relevant audit certifications, have enhanced focus on information security risks and the impact of regulations, such as Sarbanes-Oxley.
As the regulatory landscape changes and technologies allow greater avenues for information sharing, IT audits will continue to grow in scope and importance. The overall purpose of the audit is to find vulnerabilities in systems and controls and recommend solutions. If done correctly, an audit’s main function is to proactively prevent any trigger or activities that can cause harm. These negative activities, if unchecked, can hurt a company financially, legally, and reputation-wise. As such, auditing is an important success driver. But auditing doesn’t have to be a negative function in the day-to-day business of an information technology department. Auditing professionals have the ability to guide IT departments to success by partnering to create and manage reasonable and appropriate controls. Taking a proactive approach to auditing can lead to greater audit success for the IT department: You can be proactive by sharing information, facilitating a partnership with auditors, and identifying shared goals.
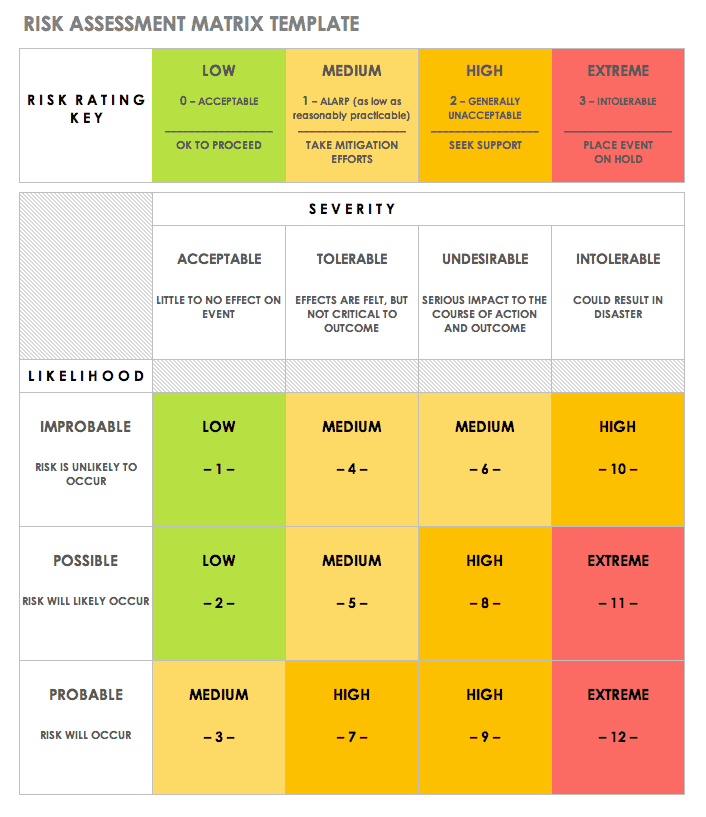
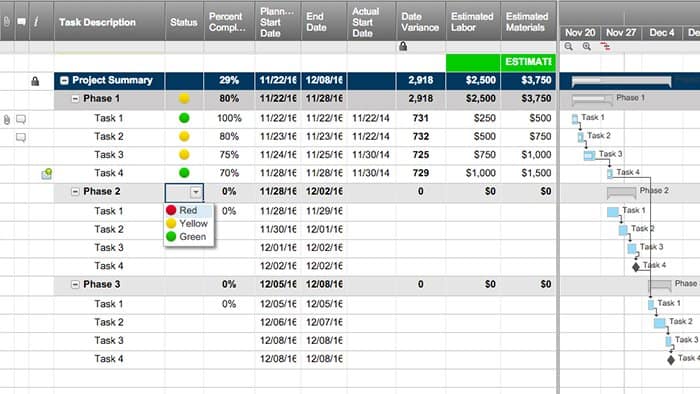
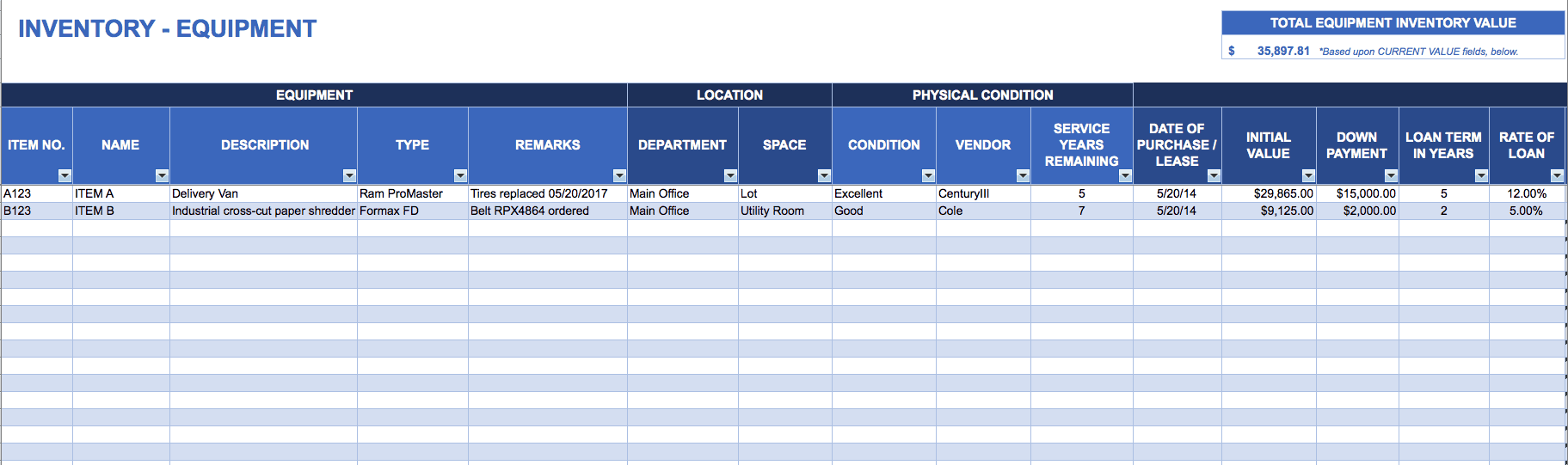
Templates provide a helpful, standardized way to get started planning for audits and to assess your practices before the audit occurs. The following three templates are free to download and completely customizable.
Download Project Risk Assessment Template
Create Audit Project Plan Template in Smartsheet
Download Equipment Inventory Tracking and Management Template
Improve IT Audits with Smartsheet for IT & Ops
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.