What Is an Audit Trail?
Audit trails are secure records that catalog events or procedures to provide support documentation. They are used to authenticate security and operational actions, mitigate challenges, or provide proof of compliance and operational integrity.
Numerous industries use versions of an audit trail to provide a historical record of progression based on a sequence of events. Whether it is logging the design changes of a product build, keeping the record of financial transactions for an e-commerce site, communication transactions, healthcare activity, or legitimizing the outcome of an election, an audit trail validates actions and outcomes. Audit trail records will contain details that include date, time, and user information associated with the transaction. As a result, audit trails are able to identify areas of non-compliance by providing information for audit investigations.
IT plays an important role in the general process of industry- or regulation-specific audit logs and trails. However, the department itself has a unique and densely populated log process where the numerous and varied activities of users, systems, and applications are constantly monitored to prevent misuse, hacking, or corruption of information. IT professionals use this system for validation as an essential tool to analyze operations and technical controls for computer systems. Used to validate and monitor activity, an audit trail provides a tool to maintain information and system integrity.
Auditing vs. Logging
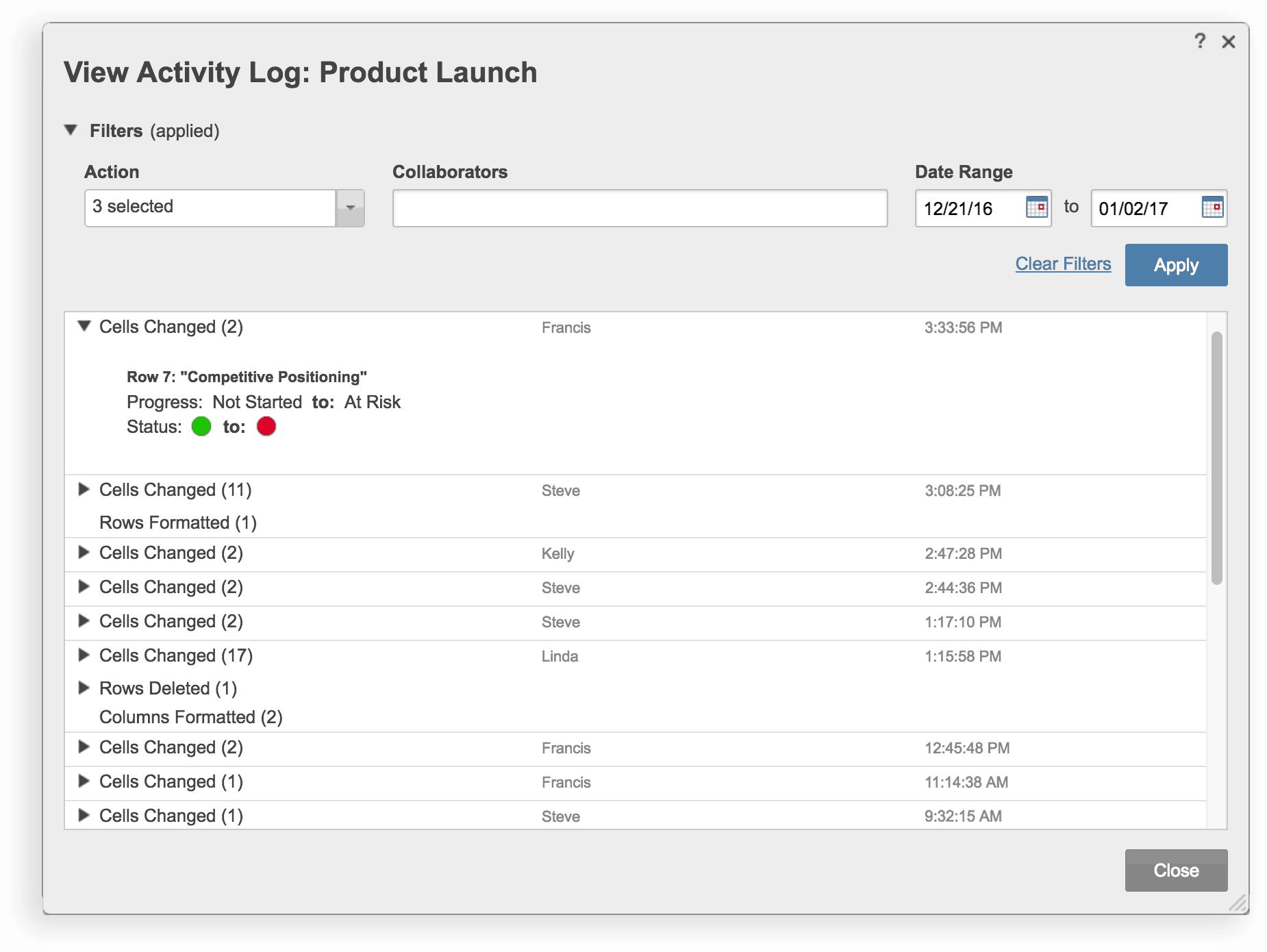
Sometimes used interchangeably, the terms auditing and logging can mean a variety of things. Systems can also maintain different types of audit trails and logs for different purposes. Logging most often has to do with program level events, such as administrative actions and abnormal related events that technical staff use for debugging software problems. This identifies system problems before they are big enough to cause harm, such as system outages or failures, which can hinder productivity. By contrast, auditing most often refers to user level transactions, such as a change to a financial record that was made by ‘Joe Smith’ at ‘10:00am’ on ‘December 21, 2016.’
Most solutions have two separate sets of logs that are maintained concurrently, including cloud platforms. For example, Google’s cloud solution maintains an administrator activity log which tracks API calls and changes to configurations, and a data access log that records updates or changes to user-provided data.
Types of Audit Trail Activities and Contents of an Audit Trail Record
An audit trail provides basic information to backtrack through the entire trail of events to its origin, usually the original creation of the record. This may include user activities, access to data, login attempts, administrator activities, or automated system activities. Audit records contain elements defined by the company which include:
- What the event was
- What user, system, or application launched the event (this information may include IP address and device type)
- The date and time the event occurred
Some audit trails look more closely at actions within certain applications to chronicle more than a simple system or application launch. These logs can pinpoint elements such as specific changes to a database or information contained therein, and can also detect improper web-browsing or email use. Many IT departments have more than one audit trail that can be system-, application-, or event-defined. Highlighting abnormal activities or use deemed "out of the ordinary" can initiate an investigation. An accurate and well-defined audit trail provides the evidence to find answers and solve issues.
How Long Do You Maintain an Audit Log?
The Sarbanes-Oxley Act declares that applicable US corporations keep their logs for at least seven years and maintain the audit trail for the life of the records if possible. Maintaining logs is useful for reporting and problem-solving in the future.
Sample Events That Should Be Audited/Logged
IT Audit Trails are constructed to address numerous activities that make up an event or series of events that can be investigated to find areas of concern. Problem activities include security breaches from hackers, in-house or out-of-house authentication problems, unauthorized usage, unusual levels of activity, or system failures. Records include the automated events scheduled through the operating system (OS), network access, application events, and manual activities of the various users. Normal activity may include accessing applications and system authentication.
However, when an unusual or abnormal use is detected such as large-scale data change, application failures, or unauthorized access, the system provides means to follow a trail to identify the problem and then remediate. Other unusual activity that could arise may be inconsistent patterns of activity by users, attempts to bypass systems or protocols, large scale changes to the information, and unusual internet activity.
How Often Do You Review an Audit Log?
Each company’s frequency will vary, but the National Institute of Standards and Technology (NIST) suggests conducting periodic audits of review logs as often as necessary according to their industry and security needs.
In some instances, regulations may dictate a specific time frame in which logs must be reviewed. For example, if you have an audit committee involved with your business, they may define a regularly scheduled review, such as bi-annually or annually.
Types of Industries That Rely on Audit Trails
The need to support compliance, security, and operations is found in most (if not all) industries. The laws that both mandate and regulate the use of electronic records make audit records an important element in defending against security breaches, supporting compliance reporting, and ultimately passing numerous kinds of internal and external audits. Industries that have provisions to track information integrity include government agencies and universities who maintain sensitive, confidential information, and any company that uses electronic records containing confidential information. Each industry, whether tracking records or transactions, will benefit from maintaining accurate audit logs.
Industry uses of audit trails include:
- Financial, accounting, and billing records
- Manufacturing design controls
- Health information
- Clinical research data
- IT helpdesk records
- Content management version control
- University student records
- E-commerce sales
- Legal and research investigations
- Nursing medical records
- Ballot-keeping and voting records
To that end, there is a growing need for industries as well as government and educational agencies to maintain and provide accurate and auditable information. If an organization is utilizing a database management system to manage records, chances are high that they record audit trails.
The Importance of an Audit Trail
The audit trail provides a “baseline” for analysis or an audit when initiating an investigation. The purpose or importance of an audit trail takes many forms depending on the organization: A company may use the audit trail for reconciliation, historical reports, future budget planning, tax or other audit compliance, crime investigation, and/or risk management.
Who Uses an Audit Trail?
Audit trails are managed by staff within the IT department. Any user who touches the electronic record will be included in the audit trail. This user may be a human or electronic system that automatically makes updates and changes.
Benefits of an Audit Trail
The ability to follow records back to their origin provides numerous benefits, including transparency and a defense of records for compliance, record integrity and accuracy, system protection from misuse or harm, and security of sensitive or vital information. These are achieved through these four areas:
- User Accountability: A user is anyone who has access to the system. Implementing audit trails promotes appropriate user behavior, which can prevent the introduction of viruses, improper use of information, and unauthorized use or modifications. In addition, the user knows that their actions are automatically recorded and tied to their unique identity.
- Reconstruction of Events: When an investigation is warranted or triggered, the first step to remediate a problem is knowing the "when,” the “how," and the "what" of the event. Visibility into this information can aid in problem detection and prevent future occurrences of things such as hacking, system failures, outages, or corruption of information.
- Intrusion Detection: Audit trails aid in identifying suspicious behavior or actions. Unauthorized access is a serious problem for most systems. Many regulations now have mandates for the security of information and maintaining confidentiality. Protection also extends to intellectual property, designs, personnel information, and financial records.
- Other Problem Identification: Through real-time monitoring, you can use automated audit logs to identify problems that indicate system implementation issues, operational issues, unusual or suspicious activities, or system and operator errors.
The Importance of Audit Trails for Compliance
Since most industries today fall under several regulatory statutes either in the U.S. or internationally, those entities, especially those that keep electronic records, should maintain a strong and accurate audit log and trail system. The IT department plays a vital role in the maintenance, security, availability, and integrity of the records to provide auditable information for the defense of industry compliance.
Regulatory statutes such as the Health Insurance Portability Act (HIPAA), Sarbanes-Oxley (SOX), and Gramm-Leach-Bliley Act (GLBA) not only have demands for the proper maintenance of electronic records, but also mechanisms for proper compliance and audit. Most industries use the support of IT services to maintain their electronic records in order to control record keeping, provide appropriate and protected user access, and strong privacy controls that they can track and mitigate. The industries most in need of sound audit trail policies include financial services, communications, e-commerce sites, universities, and health care services and providers.
The Importance of Audit Trails in Healthcare Organizations
Healthcare organizations are required to abide by stringent security measures and remain compliant with the HIPAA guidelines, meaning audit trails and logs are extremely necessary to accurately track who has access to protected health information (PHI), when secure data and information was accessed, and the reasons for access.
HIPAA regulations mandate that healthcare organizations implement procedures to regularly review and manage how information is stored and accessed. Audit trails help to provide visibility into this information, creating a system to accurately review historical security and operational activity, improve the way information is stored, and secure authorized access to it.
Since healthcare companies must always remain compliant and regularly audit their processes and information access, they need a tool to help them keep track of changes in authorization, provide critical information for reviews, and ensure that the integrity of their systems is not in jeopardy.
Smartsheet is a work execution platform that enables healthcare companies to improve auditing processes, manage PHI, and track and store auditable records in one centralized location, while meeting or exceeding all of HIPAA’s regulatory requirements. Streamline reporting, organize all necessary information in one centralized location, and set security and sharing settings to uphold data security standards.
Interested in learning more about how Smartsheet can help you maximize your efforts? Discover Smartsheet for Healthcare.
Tips to Keep in Mind
Audit trails are most effective if they are automated. While many systems emphasize protection from outside breaches, real-time audit trail reports can also red-flag suspicious in-house activity or misuse. Where the logs reside and who has access is also critical when maintaining audit trail integrity. Knowing what information to include in the logs is another key issue. It is recommended that the logs include basic information, at a minimum, such as who was involved, date and time, and what happened, but there may be other specific information to add which is dependent on security needs, industry expectations, and reporting requirements.
Important tips regarding audit trails include:
- Ensure audit trail information is stored in a secure location and backed up regularly.
- Only collect useful and necessary information in the audit trail to avoid storage capacity issues.
- Review audit logs on a scheduled basis in order to mitigate risk.
- Coordinate with system stakeholders to ensure the security and availability of their system’s audit trails.
- Keep IT and leadership across appropriate business departments informed on all audit activity.
Tools for Analyzing Audit Trails
The sheer number of events included in an audit trail calls for automating the collection of audit trail information. Tools that have trend analysis and detections for unusual use can catch hostile or non-hostile breaches. Red-flag warnings for unauthorized log-ins (whether successful or not) provide attack detection. Functions that follow defined user activities can identify misuse to prevent the theft or corruption of valuable data. Identifying application or system failures is also a key aspect for continuous operations and to prevent unscheduled outages or downtime.
The NIST Handbook contains a list of principles and practices for securing IT systems and includes a section on audit trails. NIST defines an audit trail as “a record of system activity by system or application processes and by user activity.” NIST recommends the following considerations in order to effectively review audit trails:
- The ability for reviewers to recognize both normal and unusual activity
- The ability to query and filter audit records for specific information
- The ability to escalate audit trail reviews if a problem is detected
- The development of review guidelines in order to identify unauthorized activities
- The use of automated tools to keep audit trail information at a minimum and also extract useful information from the collected data
Best Practices for the Audit Trail Maintenance and Review
Throughout this article, we’ve mentioned the importance of maintaining and reviewing audit trails. There are no guidelines that define a specific timeframe for maintaining records or review. However, the ability to access an audit trail associated with a current or historical record may help solve a problem. Therefore, it’s important to maintain the audit trail record for the life of the record. If you do not struggle with storage capacity issues, maintaining audit trails as long as possible can prove beneficial.
As mentioned, audit trail reviews will vary by organization and may take place quarterly or annually during a security audit. NIST recommends developing review guidelines specific to the organization in order to ensure a review takes place regularly.
Challenges Associated with Maintaining/Managing an Audit Trail
Although audit trails are common practice and automated in most technology solutions, challenges exist in maintaining or managing an audit trail including the location used for storage, size, and access. The logs may be cumbersome to navigate as they increase in size, which can cause storage cost challenges. Access may be too broad, which can compromise the integrity of the data. Occasionally, additional challenges are found in the limitations of applications. Finally, there can be disagreement on how long to keep records.
Audit trails provide the means to backtrack a vast array of problems associated with information security, access, and system optimization. The balance between system protection and operational performance should be maintained at industry appropriate levels.
Defining “normal” operations can help simplify audit trail processes by highlighting only the unusual activities that can cause harm. In this way, you can reduce the time spent reconstructing events, writing reports, and interviewing employees on events that are within the “business as usual” sphere.
However they are used, audit logs provide needed information when dealing with integrity, security, and access. Breaches or loss through inappropriate use, hacking, theft, or corruption can cost a company dearly through direct damage to profits and reputation, the costs associated with stolen proprietary or confidential information, or the pitfalls of regulatory and legal defense. When used effectively, audit logs and trails can identify problem areas, provide the means to find remedies, and protect the company from the problems associated with computer and electronic record keeping challenges.
Improve Audit Trail Management with Smartsheet for IT & Ops
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.