What Is Risk Management and Risk Management Software?
It’s important to understand who or what a risk is in the context of business projects and goals. Here are some key definitions and concepts to keep in mind as you compare risk management software solutions:
-
Risk Management in a Corporate Setting: Risk management is the ongoing process undertaken by a company to identify, evaluate, and treat potential exposure to loss, and to monitor risk factors to reduce the effects of damages or loss. Risks can be financial, reputational, competitive, legal, and regulatory.
-
Enterprise Risk Management (ERM): Enterprise risk management is an evolving field in the corporate world, with the goal of reducing risks and reducing fraud that can negatively impact an organization. Typically, ERM involves a framework that identifies risks and opportunities relevant to an organization, and measures these with the relative likelihood of it happening and the impact if it does. ERM has been evolving rapidly in the 21st century, as stakeholders want to understand the risks facing their organizations.
-
Factors Included in ERM: Typically, ERM factors include planning, strategy, and internal control. ERM also involves adhering to the Sarbanes–Oxley Act, which was enacted on the federal U.S. level in response to the Enron scandal to help ensure transparency and cooperation of publicly traded companies. These factors are evolving with the rapidly changing global business environment.
-
Risk Management and Compliance: As a result of mergers that create bigger organizations and the aftermath of the recession of 2008, regulators, governmental bodies, and debt rating agencies are increasing their scrutiny on the risk management processes of companies.
-
Risk Management Software: Sometimes known as compliance management software, risk management software helps companies identify risks associated with their assets, and displays them via a dashboard. Such software can measure and monitor virtually any kind of risk posed to an enterprise, including IT risks and data breaches.
Key Risks Small Businesses and Enterprises Face
No venture in a free-market system is entirely risk free, and not every factor critical to a business’s success is under it’s control. Therefore, it’s imperative to be as aware as possible of all potential risks that a company or organization might face. These can include:
- Financial Risks: If a division is not going to hit its sales marks for a quarter, that poses a financial risk for the entire company. Being able to discover and monitor such a risk can help a company course correct and get back on track.
-
Interest Rate Risks: Mortgage and financial institutions can face severe business consequences due to rising or falling interest rates. These companies need to plan for any possible changes to interest rates.
-
Legal Liabilities: A company may be at risk if it is the subject of litigation. Companies need to maintain adherence to all laws relevant to it on the city, county, state, and federal levels (and internationally, if applicable). Organizations also need to be aware of potential legal risks like perceived discrimination.
-
Cyber Risks: Hacking, cyber attacks, phishing, and ransomware attacks have been on the rise around the world, and no company is immune. It’s critical for companies to install security updates as soon as they are released, and take any other measures needed to protect business- and customer-critical data.
-
Uncertainty in Financial Markets: Political upheaval, elections, and global volatility can all take a toll on a company’s stock price and financial stability.
-
Governance and Regulatory Compliance: As regulations evolve over time, corporations must ensure they are evolving as well. Certain industries require detailed compliance (for example, healthcare companies must meet HIPAA compliance) which, if not followed to the letter, could result in dire penalties and consequences.
-
Natural Disasters, Accidents, and Wars. Disasters like hurricanes or terrorist attacks can pose risks to any business--from a fleet company that temporarily cannot deploy its trucks to a financial institution whose stock plummets along with world markets.
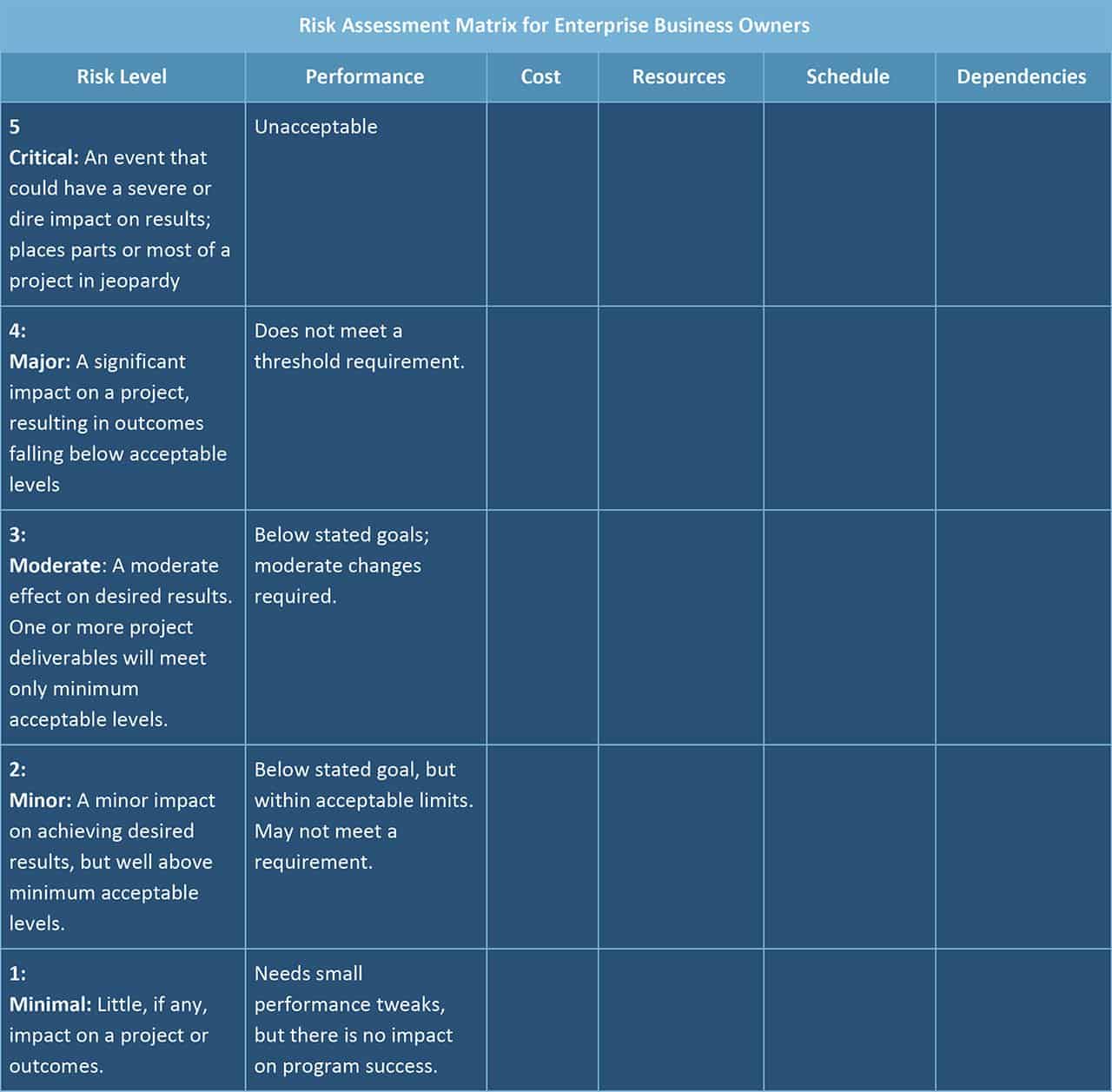
Risk Assessment Matrix for Enterprise Business Owners
Enterprise business owners can use this risk assessment matrix to list out the thresholds for measuring risk in various categories on an ongoing basis. Under “Cost,” for example, the dollar amount will vary, but a “5” would be a significant portion or even majority of a time period’s forecasted income and “1” would be a small amount. Using this matrix, an enterprise business owner can sketch out and keep track of where the biggest risks may lie, and then update it weekly or biweekly as the project progresses. Everything listed in the top two lines are usually business-critical and this matrix helps keep the most urgent issues front and center.
Issues might include IT security, global and national compliance issues if applicable, delivery of vendor shipments or contributions, launching a new product line, political unrest, and more.
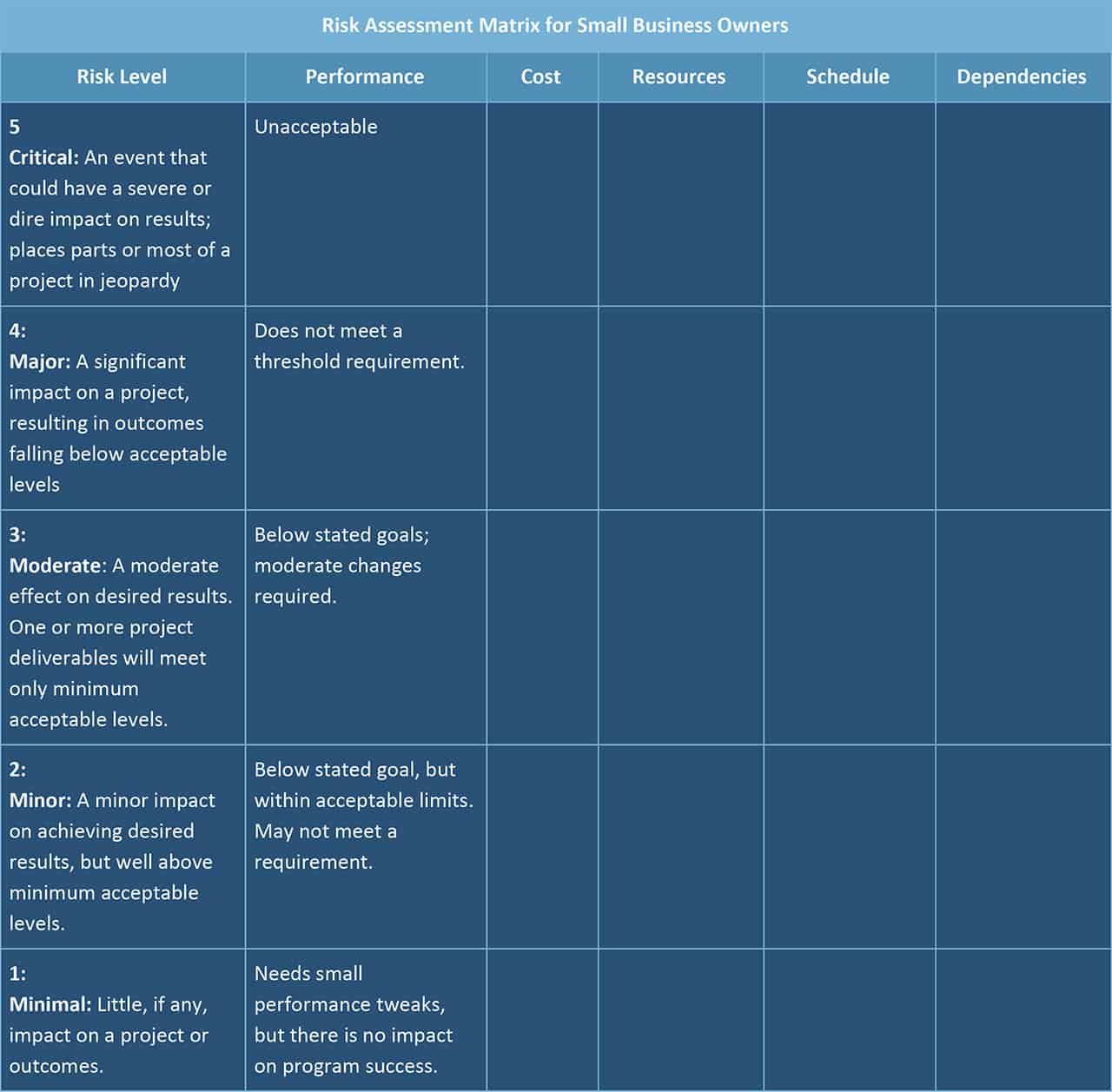
Risk Assessment Matrix for Small Business Owners
Small business owners can use this risk-assessment matrix to list out the thresholds for measuring risk in various categories on an ongoing basis. Like the matrix above, the dollar amount under “Cost” will vary for example, but a “5” would be a significant portion or even majority of the time period’s forecasted income, while “1” would be a small amount. Using this matrix, a small business owner can sketch out where the biggest risks may lie, and then update this weekly or biweekly. Everything listed in the top two lines are usually business-critical and this matrix helps keep the most urgent issues front and center.
Issues might include IT security, compliance issues if applicable, delivery of vendor shipments or contributions, launching a new product line, and more.
Key Risks Faced by the Financial Sector
From small member-owned credit unions to global investment banking institutions, the financial sector faces unique risks that could affect the holdings and net worth of their customers. Some countries require that some institutions (typically banks) belong to a network of companies that insure deposits up to a certain amount. Financial sector risks include:
- Investment Risks: No investment is guaranteed, of course, but an investment company must weigh and measure risks on behalf of their clients in a fiduciary role. Even with the best of intentions and research, however, some investments that seemed smart, even conservative, may end up virtually valueless. Enron is a classic example of an investment risk.
-
Security: Financial institutions must embrace security at every level, from securing its depositors’ accounts to executing secure transactions. Phishing is on the rise, as is ransomware, and customers may accidentally click on a malicious email, compromising (even temporarily) their accounts. Updating security systems is crucial, as is educating customers on the importance of checking emails before clicking, changing their passwords often, etc.
-
Breaks in Business Continuity: A financial institution can’t always predict the business landscape, so it must be able to pivot when businesses have breaks, merge, close, and more.
The Basel II Accord of 2006 stipulates that financial services are required to use risk management software. The international regulation requires that banks have enough cash reserves to cover the financial cost of problems in the business, including fraud and IT.
The main integrated financial trading systems, such as Misys Summit, Calypso, and Murex, have risk management and compliance at the heart of their businesses. Misys is a London-based financial conglomerate that began serving the insurance industry and now is a leading all-up financial services company. San Francisco-based Calypso Technologies provides solutions to financial trading companies around the world. Murex, based in Paris, provides software IT products and solutions to the financial sector. These companies and their solutions service hundreds of other financial companies, so it’s business-critical that they align to strict regulatory statutes, and that the companies they work with align and integrate with them accordingly.
Mark Opila is CEO of Patrina Corp., a data and records management and compliance company based in New York. The company provides solutions to the financial sector in critical compliance areas.
“One way we help our clients is by providing secure records archiving,” Opila says. “The SEC and other regulatory agencies require that financial institutions keep detailed records, some of which may need to be retained for the life of the business. That includes emails, social media posts, blotters, minute books, and more. That can seem overwhelming to an organization, so we can provide help in creating a compliant repository of all that information, in case the institution is ever asked to produce it.”
Another important financial compliance issue can occur when a brokerage shuts down, Opila explains. “Even if an institution closes and goes out of business, it has a responsibility to former clients to make arrangements for securing their records... sometimes years after the closure.”
Having these detailed records is a critical piece of compliance for financial institutions, Opila says; the need for accountability is key, even years after a transaction may have occurred.
Why IT and Software Companies Need Risk Management Tools
It’s not just software companies that must be highly attuned to IT risks. Virtually every company, large and small, now uses digital technology for transactions, databases, productivity work, and more. So it’s critical for all organizations to maintain relationships between IT risks, assets, processes, and controls with descriptions, categories, hierarchy, ownership, and visibility.
Organizations and their technology departments must assess, quantify, monitor, and manage all IT risks, from phishing and data breaches to the growing threat of ransomware. Lindsey Havens is the senior marketing manager for PhishLabs, a company providing solutions to attack, neutralize, and even prevent phishing for organizations. In Havens’ view, phishing is one of the most serious cyber risks companies can face.
“Phishing attacks are a predominant attack method used by cybercriminals to steal account data and carry out online fraud,” Havens says. “Supported by a thriving underground ecosystem, cybercriminals can easily stage, launch, and profit from phishing attacks targeting businesses and their customers.
“Traditional approaches to defending against phishing attacks focus on shutting down the web page,” Havens continues, but adds that doing that doesn’t really reduce the risk. “This stops the immediate attack, but does little to stop the cybercriminal. With vulnerable websites and hosting providers readily available, it is easy for a cybercriminal to stage a new phishing page and continue launching attack after attack.”
A real solution comes, Havens believes, when IT leaders are well versed in issue management and remediation. This includes every stage from investigation through root cause analysis to remediation. IT must also swiftly and clearly communicate throughout the organization any new policies or protocols identified moving forward communicated.
Root Cause Analysis Templates
Lastly, each IT department should have its own system for risk monitoring, and for metrics that display risks, assess their likelihood, and offer solutions to rectify any issues. Many software solutions provide full-stack visibility, to give an all-up view of where IT issues might exist, in order to address them quickly.
Compliance and Governance Risk Management
Regulatory agencies and their authority vary from state to state and country to country. But many industries require governmental regulation and compliance. Some of these include privately owned utilities, healthcare organizations, financial institutions, health insurance companies, alcoholic beverage companies, interstate commerce companies, fleet managers, and more. Risks to these industries can lie in noncompliance with various regulations that apply to their industries, which can differ from state to state and even city to city.
In the insurance industry, the word risk is used slightly differently. Insurance companies must calculate risks per type of population, as well as probabilities of occurrence. In setting rates for, say, wildfire damage homeowner insurance, a company must weigh the probability a home might be damaged in a wildfire--even if the home is located in the middle of a large city. An insurance company may consider a population’s general health when it is setting premiums and copayments for types of procedures, as well.
In the healthcare industry, organizations of every size need to ensure compliance with the 1996 Health Insurance Portability and Accountability Act (HIPAA). This legislation regulates the privacy and security of individuals’ healthcare information. In general, a person’s healthcare information cannot be shared with others without that person’s explicit permission. Hospitals, blood banks, and all other healthcare providers must comply with the act; failure to do so exposes not only the patient to potential harm, but the institutions to enormous liability claims if it compromises sensitive patient information.
Khoi Do is the Manager of Advisory Services and International Business Development at UL EHS Sustainability. One of the company’s initiatives is the PURE platform, the industry’s first integrated environment, health, safety, and sustainability software solution designed to drive business performance, manage operational risks, and improve day-to-day performance.
“It’s important to anticipate the changes in regulations and compliance so that a company can be ready and already in compliance when a new regulation takes place,” says Do. “It used to be that a governing body like the World Trade Organization (WTO) might say a regulation would be introduced on a certain date, and affiliate organizations would have a period of time to comply. Now, the WTO might say a certain policy is going into effect in 90 days - and that means that all organizations need to have that new policy incorporated by that date.”
How to Handle Risk Management in Projects
On a smaller scale than company- or enterprise-wide, individual projects can also face risk, which software solutions can track and manage. Projects can face budget risks, timeline risks, incidents, emergencies, opportunities, and more. Project managers can perform a risk assessment for all aspects of a complex project and then get high-level views into where risks may lie, how to mitigate and address them and get back on track, and how to share data insights. An enterprise or small business risk management software solution often has customizable individual features for assessing and managing risks on individual projects.
For project managers, it’s helpful to think of “if/then” scenarios and list and assess potential risks at the beginning of each project. . For instance, “if we go over budget in this first phase, then XX will happen or need to happen”-- XX being reducing the scope of future phases, for instance, to make up for lost money, or requesting a shift of resources from one part of the project to another.
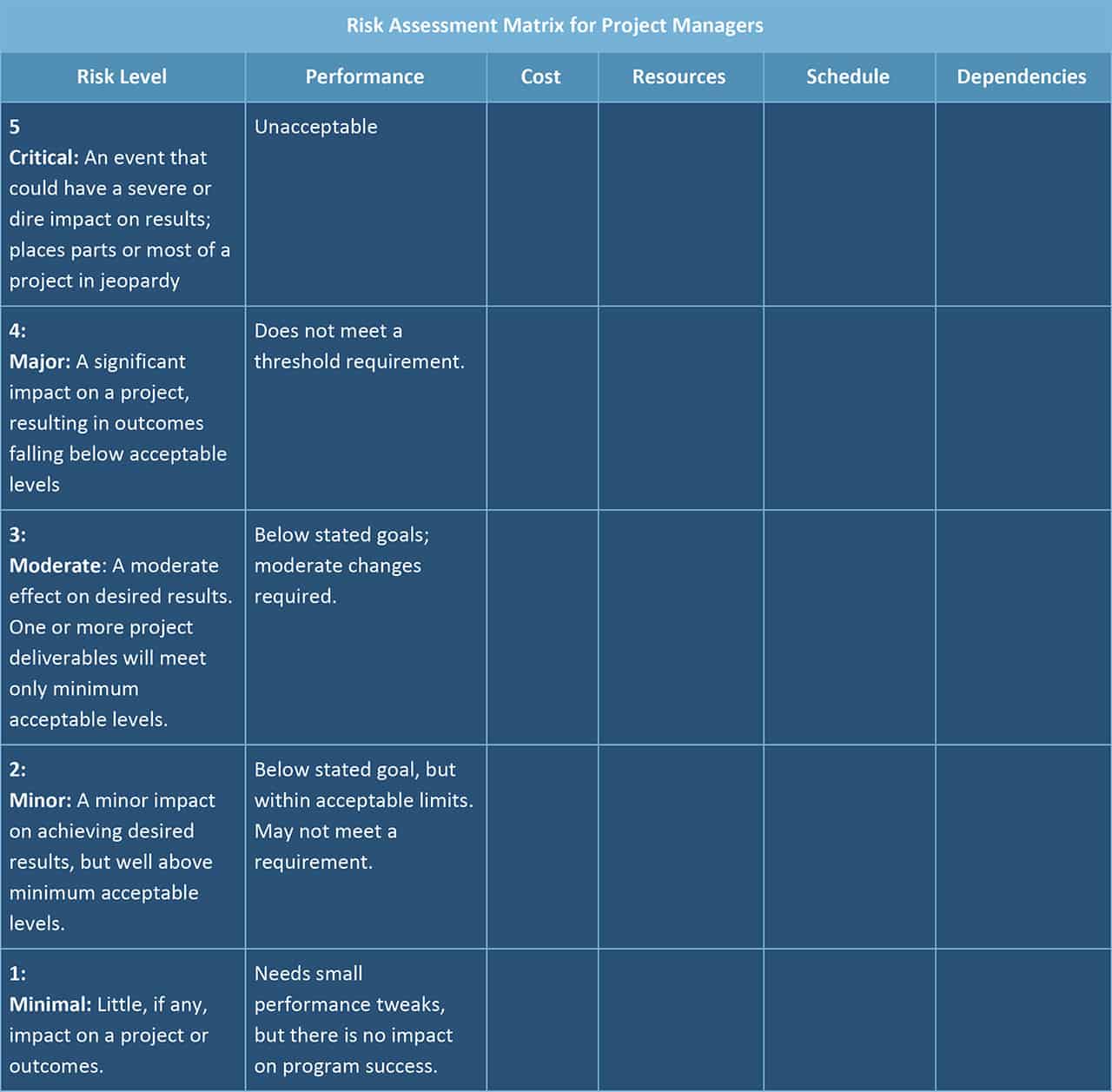
Risk-Assessment Matrix for Project Managers
Project managers can use this risk-assessment matrix to list out the thresholds for measuring risk at the beginning of a project. Under “Cost,” for example, the dollar amount will vary, but a “5” would be a significant portion or even majority of the project’s cost; “1” would be a small amount. Using this, a project manager can sketch out where the biggest risks may lie, and then update this weekly or biweekly as the project progresses. Everything listed in the top two lines are usually business- and project-critical and this matrix helps keep the most urgent issues front and center.
Risks Posed by Vendors: Companies Must Be Proactive
Companies can face risks through actions posed by a vendor or a third party. It’s critical to protect confidential, proprietary, or classified information, and organizations often take a huge risk by entrusting such data to an outside operator. Here are some risks that vendors can pose to organizations of any size:
- Breach of legal or compliance regulations, especially with governmental, financial-sector, and military contractors.
- Breach of HIPAA regulations that require protected health information (PHI) to be secure.
- General legal issues, which can result in lawsuits, termination of relationships, loss of work, and more.
- Data security, since companies must determine which vendors get what level of access, and how. For example, Will a vendor temporarily use a company-provided laptop with embedded security to gain access to sensitive data for a project?
- Loss of intellectual property, if a vendor has access to proprietary information and then compromises or steals it to use and present as their own.
These are just a few of the risks posed by vendor and third-party relationships - all of which could result in severe losses to the company, including fines if laws were broken. To learn more about vendor management, check out the Definitive Guide to Vendor Relationship Management. And learn how to create and use a vendor risk management maturity model.
Supply Chain Risk Management: How to Plan for the Unplanned
One of the challenges that Do at UL EHS Sustainability helps clients with is supply chain risks. “We always recommend that clients stress-test their supply chains for different scenarios,” Do says.
Around the world, there may be geo-political changes, regime changes, natural disasters, and other events that can affect a supply chain and put it at risk, he notes. “If your company sources 25 percent of a resource from a country in Southeast Asia, for instance, and a tsunami hits that country, you will be facing a potentially huge issue -- unless you have identified backup sources and diversify where your products come from,” Do explains.
Doing that advance planning for “what-if,” Do says, means risk is mitigated, and operations stay on track. And that diversification is something that any company should do before any extreme change affects its supply chain so that it’s prepared to go to Plan B when necessary.
As for supply-chain-specific software solutions, Do says it should have three key elements:
- Easy to use interface, for your company and your suppliers. If suppliers don’t adopt the tool, it won’t help the process.
- Data to spot trends and enable workflows. Suppose you have 500 suppliers, and 10 questions each must answer. If your supply-chain risk management tool shows that 60 percent of the responses to one of those questions is not in line with expectations, that’s a sign to more closely inspect what may be going on there. It could be a glitch in the wording of a question, or it might be an indicator of a pattern that you should address, the earlier, the better, Do advises.
- Business insights to predict opportunities and perhaps identify that backup roster of suppliers if the need should arise.
Managing the Risks: The Benefits of Risk Management Software
Since no industry or company can operate without risk, the right risk management solution or tools can help an organization identify, monitor, and mitigate risks far more efficiently than it could by human power alone. Some of the benefits of using an appropriate risk management software include:
- Increased Shareholder Value: A company that manages and mitigates its risks will have a better brand and reputation, which in turn can boost stock prices.
- Optimized Risk and Return Outcomes: You can often customize software to help ensure maximum efficiency and minimum loss.
- Greater Transparency: Managers are able to tackle and prioritize projects with the best risk/reward outcomes.
- Higher-risk Initiatives Can Get More Scrutiny: You can closely monitor and manage the projects that are riskier, but still important to a company.
- Reduced Compliance and Legal Costs: Integrating corporate governance and risk management and compliance processes means lower costs for all.
- Internal Controls: Organizations that monitor and manage their risk have deeper ownership of their operations than those that don’t use risk management software. Controlling and monitoring risk in an intelligent, scalable way means a company has a full view of its business landscape.
- Strengthened Operations: Again, the more knowledge an organization has, the stronger it can be. Knowing where risks lie and what efforts are being undertaken to mitigate them lets managers breathe a little easier and deploy resources where and when they are needed.
- Likelihood to Refresh and Upgrade Security Regularly: Using a risk management software system is part and parcel of a sophisticated approach to IT in general. Updating and scaling a risk management system goes along with updating an operating system security, with enhanced cloud or hybrid security solutions, and more.
How Does Risk Management Software Work?
Risk management software typically identifies the risks associated with a given set of assets and then communicates that risk to the business so they can take action. In other words, whatever risks a company might face -- security data breaches, IT compromises, drops in sales, non-compliance in regulated transactions -- there is risk management software that can help monitor, detect and propose remedies. Usually, you configure risk management software of any type to create an at-a-glance dashboard to show the evolution of risks and issues, to pinpoint where problems may lie, either today or in the future, including emergencies like data breaches, but also ongoing issues like sales figures being slightly down. The software collects data from throughout the business to indicate where risks might lie. Risk management software typically identifies the risks associated with a given set of assets and then communicates that risk to the business so they can take action. In other words, whatever risks a company might face -- security data breaches, IT compromises, drops in sales, non-compliance in regulated transactions -- there is risk management software that can help monitor, detect and propose remedies. Usually, you configure risk management software of any type to create an at-a-glance dashboard to show the evolution of risks and issues, to pinpoint where problems may lie, either today or in the future, including emergencies like data breaches, but also ongoing issues like sales figures being slightly down. The software collects data from throughout the business to indicate where risks might lie.
Challenges in Implementing Risk Management Software
It’s one thing to agree as a company, in theory, that risk management software is a good investment and a solid idea, but there can be hurdles involved. Linking siloed systems can be costly at the outset. Getting buy-in from major stakeholders and directors across the enterprise may pose a challenge; some may resist change. Finally, any risk management software solution is truly only as powerful as the people who administer it, as well as the solution’s own ability to scale and adapt, such as offering RSS feeds and other functions, as regulations and other risk and compliance issues change and grow.
Top Features to Consider in Selecting a Risk Management Software Solution
When considering a risk management software solution for your company, experts agree that these are the top factors and features to consider:
Download Risk Management Software Checklist
Be sure to spell out who will conduct ongoing check-ins and measure efforts, and how that process works. There should be accountability and transparency for both the people who use the software and those who must work with its results.
Also, there are both paid and open-source/free risk management software solutions. Here are some factors to keep in mind when comparing open source vs. paid solutions:
Open-source and free options: There are some open-source risk management software solutions that offer good basic features and functionality. They include:
- IntelligenceBank GRC: Designed for the financial services industry, this option includes the ability to create custom landing pages, configure an RSS feed for notifications on industry and compliance changes, connect via API to all relevant sites, and more.
- Eramba: Key features include the ability to manage controls and audits, exception management, and policy management. Supplies IT risk management solutions for healthcare, financial services, education, and other verticals.
- SpiceWorks: A free tool, though it’s not open-source. SpiceWorks focuses on managing inventory of devices and tools for risk management.
- SimpleRisk: A basic free package that helps set up risk monitoring and mitigation processes, but you’ll have to pay for the full suite.
- Practical Threat Analysis Technologies: Free tools to help organizations find solutions to secure their systems and technology.
- Nagios: Provides ongoing system monitoring for mitigating risks.
Paid/subscription options: A growing number of competitive companies offer risk management solutions, some are for general use and while others are for specific industries. They include:
- NetSuite: A full enterprise management suite that includes a number of well-reviewed risk management features.
- LockPath: Its Keylight platform is a full suite of compliance-related software to help reduce regulatory risk and enforce and ensure compliance. There is a central framework to help align a company’s structure and processes to all external regulatory needs.
- ZenGRC: This solution is known for flexible, customizable dashboards for easy compliance setup and follow-through.
- ERA Environmental: Provides an all-up health and environmental risk tracking and monitoring.
- SafetySync: Highly-rated solution for worker safety risk management designed for small business and enterprise.
Creating an Effective Risk Management Framework
To create an effective program for managing corporate risks, experts advise being as thorough, transparent, and forward-looking as possible. These steps can be helpful:
- Recognize and spell out all challenges. In this era of cloud computing and regulatory adaptations, security and compliance are always evolving. Break down the cost, the regulatory and compliance bodies, and the amount of resources required to manage the relationship and potential risks.
- Ensure that the entire corporation is on board with the plan and that there is buy-in from the top executives, especially compliance officials and the legal department.
- Ensure that all third-party contacts address the “right to audit” as well as security requirements.
- Identify and document how monitoring of risks will occur throughout the enterprise, how you’ll conduct reviews and provide feedback, and how you’ll identify and resolve risks.
- Create and use a risk management matrix.
Risk Management Software Educational Opportunities
There are dozens of entities and resources available for businesses and others who do business with vendors and third parties. Since working with other people and groups involves risk in and of itself, it’s critical to have as much education as possible, and to encourage the same of your vendors. Here are some helpful resources:
- North Carolina State University program
- Marquette University program
- The U.S. Comptroller of the Currency, part of the U.S. Department of the Treasury, oversees financial institutions governance.
- The International Association of Privacy Professionals is a nonprofit and the largest and most comprehensive global information privacy community. Founded in 2000, the IAPP helps define, support, and improve the privacy profession globally.
- Risk management certification programs
Smartsheet: An Essential Tool for Risk Management Professionals
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.