What Is Regulatory Compliance?
Regulatory compliance, also called business compliance, refers to any organization’s obedience to the laws, regulations, and other rules that govern all organizations.
What Is a Regulatory Requirement?
A regulatory requirement is a rule that a government entity imposes on an organization. Some federal and state laws govern virtually all organizations. Regulations govern how organizations manage their business and employees and how they interact with customers, among many other areas.
Number of Regulations Balloon in Recent Decades
There have been attempts to decrease or slow the growth of federal regulations in recent years. Still, the overall number of regulations has grown significantly over the past several decades. A 2017 U.S. Chamber of Commerce Foundation report that assessed only federal regulations found that “Over the last 60 years, the U.S population has increased by 98 percent, while the federal regulatory code has increased by 850 percent, including some 6,081 final rules published between 2015 and 2016.”
Overall Goals of Regulations
Generally, regulations are implemented to protect someone or something, whether it be employees, consumers, the public at large, or the integrity of commerce or of business processes. The entities overseeing regulation often focus on several primary areas, including the following:
- Establishing and implementing controls at organizations
- Keeping abreast of and assessing how organizations are complying with laws and regulations
- Identifying and remediating areas where organizations are not complying
- Providing ways for organizations to report on their compliance with laws and regulations
Industries and Other Areas Where Regulations Are Prevalent
Some regulations apply to almost all organizations and businesses. But, many regulations — often federal, but also some state and local — apply to specific industries or specific areas of oversight.
Here are some regulations that apply to specific industries, areas of commerce, or other entities:
- Financial institutions and transactions
- Healthcare
- Employment and labor law (see details below)
- Environmental, including the following:
- Pollution and climate change
- Use and disposal of chemicals
- Business and tax code, including the following:
- Corporate identity and business structure, including recording and reporting
- Tax code and taxation requirements
- Antitrust laws
- State licensing
- Interstate commerce laws
- License and permitting laws
- Consumer protection, including product liability and safety
- Technology/data security, including data protection and privacy
- Energy
- Government, including public procurement
- Other areas, including the following:
- Telecommunications, media, and technology
- Other European Union regulatory matters, including agriculture, import/export, pharmaceutical and medical devices, sports and gaming, and specific product regulation
- Contract laws
What Is Compliance in the Workplace?
A wide range of regulations apply to employment and the workplace. These regulations concern the following aspects of your business:
- Employee discipline and termination
- Hiring practices
- Sexual harassment, intimidation, or other offensive acts
- Discriminatory hiring or unfair employment practices
- Wages and hours
- Work environment
- Workplace safety
- Recruitment and retention of employees
Regulations and Regulatory Compliance in Nations Outside the U.S.
Countries outside the United States also have a wide range of regulations, of course. Here’s an overview on regulations in four countries:
- Australia: The nation has a range of financial regulations, overseen especially by the Reserve Bank of Australia, the Australian Prudential Regulation Authority, the Australian Securities and Investments Commission, and the Australian Competition and Consumer Commission. Other important national regulators include the Australian Communications and Media Authority, for issues relating to the internet, broadcast, and communication; the Therapeutic Goods Administration, for medical devices and drugs; and the Clean Energy Regulator, for the oversight of energy and carbon emission issues.
- Canada: The nation has two independent bodies that oversee most financial entities in Canada. The Office of the Superintendent of Financial Institutions regulates banks, insurance companies, and other financial entities and transactions. Meanwhile, the Financial Transactions and Reports Analysis Centre of Canada works to detect money laundering and also gathers and analyzes information on possible financing of and by terrorist organizations.
Unlike most nations, Canada does not have a federal regulator of securities. Entities within provinces and territories work together to regulate securities trading. Other Canadian regulators include the following: Environment and Climate Change Canada, which oversees regulations relating to the environment and alternative energy; Health Canada, which oversees public health; and the Canadian Food Inspection Agency, which oversees food safety and animal health. - India: India has regulations at the local, state, and national level. Many of its regulations fall into three areas: economic, environmental, and public interest-related. Many of these regulations are implemented at the national level.
- United Kingdom: The United Kingdom has a wide range of regulations, some of them specific to the U.K. and some of them set up by European Union legislation. The U.K. Corporate Governance Code governs how publicly traded companies in the U.K. are set up and operate. The code focuses particularly on best practices by boards of directors in corporate governance.
Specific Laws and Regulations by Industry and Public Interest
Tens of thousands of laws and regulations apply to organizations across the U.S. In many cases, these laws and regulations apply to companies within certain industries or apply in certain subject areas. Examples of specific laws in particular industries or areas include the following:
- Financial:
- Dodd-Frank Act: Passed in 2010, this act created regulations to increase transparency and accountability within the financial industry.
- Payment Card Industry Data Security Standard (PCI DSS): Established not by government but by the four major credit card companies, this standard sets policies to increase the security of transactions involving credit and debit cards.
- Sarbanes-Oxley Act (SOX): This federal law set up a wide range of auditing and financial regulations for publicly traded companies. The law was created to decrease accounting errors and fraud. Read more about Sarbanes-Oxley here.
- Gramm–Leach–Bliley Act (GLBA): This act removed regulatory barriers that banned commercial banks, investment banks, securities firms, and insurance companies from consolidating.
- Fair Credit Reporting Act of 1970: This act regulates the collection of credit information and access to a person’s credit reports.
- Sherman Act of 1890: This is a landmark U.S. antitrust law that prohibits anti-competitive agreements between companies and other business conduct that might lead to a monopoly in a market.
- Securities Exchange Act of 1934: This act, which created the Securities and Exchange Commission (SEC), governs securities transactions in the U.S..
- Securities Act of 1933: Approved after the stock market crash of 1929, this act was intended to increase transparency in financial statements and decrease fraud.
- Bank Secrecy Act (BSA): This act requires that financial institutions assist the U.S. government in detecting and preventing money laundering.
- Technology/Data Security:
- Federal Information Security Management Act (FISMA): This act requires federal agencies to implement programs to keep their information technology systems secure from data breaches and other outside intrusions.
- European Union Data Protection Directive (EUDPD): This 1995 directive by the European Union regulates the processing of an individual’s personal data. (This law was later superseded by the European Union’s General Data Protection Regulation of 2016.)
- General Data Protection Regulation: This is an updated EU law regulating the personal data of EU citizens.
- Finnish Personal Data Act: This legislation, approved by Finland in 1999, protects and regulates the personal data of the country’s citizens.
- Danish Act on Processing of Personal Data: This legislation protects the personal data of Denmark’s citizens.
- Austrian Federal Act Concerning the Protection of Personal Data: This legislation protects the personal data of Austria’s citizens.
- California Senate Bill 1386: This is a California law that requires any company that experiences a data breach to notify any California citizens whose information may likely be exposed as part of that breach.
- Healthcare:
- Health Insurance Portability and Accountability Act (HIPAA): Among other things, this act protects health insurance coverage for workers when they change jobs and regulates how hospitals, insurers, and other groups use and disclose certain health information about individuals.
- Joint Commission (Healthcare): A nonprofit organization that accredits hospitals and health organizations and programs in the U.S.
- Civil Rights:
- Civil Rights Act of 1964: This is a U.S. law that bans discrimination based on a person’s race, sex, national origin, or religion.
- Americans with Disabilities Act: This act bans discrimination based on a person’s disability.
- Employment/Workplace:
- Fair Labor Standards Act (FLSA): This act sets the minimum wage, overtime pay, and other standards for workers in the U.S. You can find free overtime authorization templates here.
- Family and Medical Leave Act (FMLA): This act requires most U.S. employers to give employees unpaid leave for certain medical and family reasons.
- Workers’ Compensation Laws: These are state laws that require employers to pay for employees who are injured on the job.
- Worker Adjustment and Retraining Notification Act of 2003 (WARN): This act requires employers with 100 or more employees to notify workers 60 days in advance of any plant closings or large layoffs.
- Equal Pay Act of 1963: This act was aimed at ending wage disparities based on gender.
- Federal Workers' Compensation Act: This act established compensation to federal workers who are injured on the job.
- Uniformed Services Employment and Reemployment Rights Act (USERRA): This act protects civilian job rights for members of the military and military reserves while they are on military duty.
- Environmental:
- Hazard Analysis and Critical Control Points (HACCP): This is a system that addresses food safety issues.
- Immigration:
- Immigration and Nationality Act of 1952: This act governs immigration and citizenship in the U.S..
- Migrant and Seasonal Agricultural Worker Protection Act: This act sets employment, housing, and other standards for seasonal farm workers in the U.S..
- Other:
- Employee Retirement Income Security Act (ERISA): This act governs employee benefit plans in the U.S..
- Social Security Act of 1935: This act established the Social Security system of benefits for retired and disabled U.S. citizens.
- USA PATRIOT Act: This 2001 law established protections against terrorism in the U.S.
Industries Most Affected by Regulatory Compliance
Regulations are especially wide-ranging and complex within certain industries. The following are among the most heavily regulated industries:
- Financial services
- Health care
- Life sciences
- Information technology
Regulations Governing Internal Requirements for Businesses
Governments — often state governments — require companies incorporated within a state to keep and provide records relating to the operation of business. Those requirements might apply to the following elements of a business:
- Information about annual directors’ meetings
- A company’s bylaws and updates of those bylaws
- A company’s provision of stock to shareholders
- All of a company’s stock transfers
- Company records on major business transactions
- Updates or important changes to the operations of a company
Agencies That Oversee or Provide Guidance on Regulatory Compliance
Hundreds of local, state, and federal agencies administer laws and regulations that apply to organizations. Those agencies, and sometimes other groups, also provide guidance to help companies understand and follow the laws and regulations that apply to them. Some of those agencies and groups include the following:
- U.S. Securities and Exchange Commission (SEC): The SEC administers a wide range of laws and regulations that apply to the United States’ securities exchanges and publicly traded companies.
- U.S. Office of Foreign Assets Control (OFAC): This entity enforces trade sanctions that the U.S. may impose on foreign governments, organizations, and people.
- United States Sentencing Commission: This government agency has provided guidelines on compliance relating to federal criminal laws that organizations and companies must follow.
- Small Business Administration (SBA) and (its website) Business.gov: The SBA provides a wide range of information that can help businesses understand and comply with regulations.
- Equal Employment Opportunity Commission (EEOC): This agency administers laws and regulations that apply to companies’ hiring practices. It focuses on employment discrimination against people based on their race, gender, religion, age, or other such factors.
- Employee Benefits Security Administration (EBSA): This body enforces laws and regulations relating to employee benefit plans.
- Civil Rights Center with Federal Department of Labor: This entity enforces rights guaranteed by the Civil Rights Act of 1964, which includes an employee’s right to do their job without any discrimination based on race, gender, or other such factors.
- Occupational Safety and Health Administration: This agency administers laws and regulations relating to workplace safety.
- Employment and Training Administration of Federal Department of Labor: This government entity administers laws and regulations relating to companies laying off a large group of employees at the same time. It includes a requirement that businesses with 100 or more employees notify workers at least 60 days in advance of a planned layoff.
- Environmental Protection Agency (EPA): This agency administers laws and regulations that relate to how businesses’ operations affect the natural environment.
- Federal Financial Institutions Examination Council (FFIEC): The FFIEC consists of a group of five financial regulatory agencies that together oversee the Gramm-Leach-Bliley Act, which, among other things, requires financial institutions to protect the privacy of financial information they have about individuals.
Non-Governmental Entities That Oversee Industry Standards and Regulations
Some industry-related organizations have established standards that serve as quasi-regulations within specific industries. Other nonprofits have been established to oversee certain industries and regulations, including the following:
- American Society of Mechanical Engineers (ASME): This industry organization has developed rules to ensure that products meet safety, security, and other engineering standards.
- Financial Industry Regulatory Authority (FINRA): This is a nonprofit group authorized by Congress to oversee securities brokerage firms and brokers in the U.S. It can discipline its members for violating a wide range of FINRA rules that govern broker actions and behavior.
- Public Company Accounting Oversight Board (PCAOB): This is a nonprofit entity created by the Sarbanes-Oxley Act that oversees the auditors, and auditing behaviors, of public companies.
Standards That Help Guide Regulatory Compliance
NIST Standards: These standards were set up by the National Institute of Standards and Technology, a federal agency, to guide compliance with some regulations. - International Organization for Standardization (ISO) and ISO 19600: The ISO is an international body that sets standards in a range of industrial, commercial, and other areas. Its ISO 19600 standard offers guidance on how organizations can set up and maintain a system of compliance management.
- ISO/IEC 27002: This is a standard that recommends best practices to ensure appropriate security for information technology systems.
- COBIT: This is a framework that recommends best practices for managing and governing information technology. The COBIT framework was created by an information technology professional association called the Information Systems Audit and Control Association — now known only by its acronym, ISACA. (Learn more about information security and enterprise security here.)
What Is a Regulatory Compliance Cost?
A regulatory compliance cost is the amount of money or other resources an organization must expend to ensure it complies with all applicable regulations. For example, many regulations require detailed record-keeping that calls for employee time and other company resources.
The total economic costs for U.S. organizations to comply with all regulations is likely impossible to calculate. A 2017 report by the American Hospital Association estimated that regulations in the U.S. healthcare industry alone cost hospitals about $38.6 billion per year.
The Costs of Not Complying with Regulations
While the costs of complying with regulations can be steep, so can the costs of not complying. In fact, most experts say that the costs of the latter can be much steeper.
“Regulatory compliance is expensive,” says Marta Moakley, a lawyer and legal editor for XpertHR, an online subscription service that provides companies with legal and compliance advice on human resources issues. “But, regulatory non-compliance can be infinitely more expensive.” Here are some of the costs of non-compliance:
- Penalties: The most obvious costs, of course, are the governmental penalties for non-compliance. Fines for some minor violations — missing the deadline for filing an annual corporate report for your private business, for example — might be a few hundred dollars. But, violating SEC and other financial regulations can bring millions of dollars in fines. Hospitals that violate HIPAA patient privacy provisions can pay several millions of dollars in fines for large data breaches or repeat incidents.
The European Union’s General Data Protection Regulation applies to any organization that obtains or stores the personal data of an EU citizen. That means the regulation applies to many U.S. businesses. The maximum penalty for violating some provisions of the GDPR is €20 million, or four percent of an entity’s gross global revenue. - Scandals and Injuries to Reputation: As steep as fines can be, a much greater cost — to a company’s reputation — can occur when a company is found to have significantly violated laws or regulations. That reputation damage can affect sales and profits for years afterward. Here are three examples of significant reputation damage:
- Enron: Shares of the apparently very successful Texas energy company were trading at more than $90 in 2000. Then, in the fall of 2001, it was revealed that Enron’s actual financial condition was falsified through a wide range of accounting fraud. The stock price dropped to less than $1 by late 2001. The company filed for bankruptcy and was eventually dissolved. A number of executives pleaded guilty or were found guilty of a number of felonies, including fraud. The scandal was also a significant reason for Congress approving the Sarbanes-Oxley Act in 2002.
- Volkswagen: In 2015, it was revealed that the exhaust control equipment in the diesel engines of almost 600,000 of the company’s cars sold in the U.S. had been programmed to shut off after emissions testing was completed on the vehicles. That meant that when the vehicles were on the road, they were emitting much more pollution than the regulations allowed. Volkswagen eventually admitted to rigging nearly 11 million diesel-powered vehicles in the same way. The company has paid more than $32 billion in fines and compensation for customers.
- Wells Fargo: In April 2018, federal regulators fined Wells Fargo $1 billion for forcing customers to buy car insurance they didn’t need and for charging unfair fees to mortgage borrowers. In February 2018, the Federal Reserve punished the bank for, among other things, creating millions of fake customer accounts. The Federal Reserve imposed penalties that limit the bank’s growth until it proves it has improved its internal controls. Wells Fargo also paid $185 million in other fines and settled a class-action suit for $142 million in connection with fraudulent practices.
Complying with Regulations Improves Your Business and Saves Money
Experts say that the penalties and reputation damage from flouting regulations make one thing clear: complying with regulations saves money in the long run. There are also other benefits to regulatory compliance:
- Improve Your Organization’s System and Operations: When you comply with regulations, your organization runs more smoothly.
- Build a Positive Reputation among Employees, Customers, and the Public: Complying with regulations expands your credibility and legitimacy both inside and outside the company.
- Achieve Higher Employee Productivity and Higher Employee Retention: “I encourage employers to view compliance as a smart business decision,” says XpertHR’s Moakley. “It emphasizes a fair and safe workplace. Employees will probably be more productive, and employee turnover costs will be at a more reasonable level.”
- Mitigate Punishment If You Are Found to Have Violated Regulations: A strong compliance program can also help your company, even if it has been found to have violated regulations. The U.S. Department of Justice and the Securities and Exchange Commission enforce U.S. laws prohibiting the bribery of foreign officials. If a company is found to have violated the bribery laws, fines can be millions of dollars, says Kristy Grant-Hart, author of How to be a Wildly Effective Compliance Officer and CEO of Spark Compliance, which has offices in London, Los Angeles, and Atlanta. “If you are investigated for bribery or fraud, the federal sentencing guidelines give you credit for having a good compliance program in place,” Grant-Hart says. The compliance program can be evidence to the regulators that the problems came from rogue employees and not from a company culture that doesn’t believe in compliance, Grant-Hart adds.
Moakley says that companies need to understand “that compliance overall is good business. I think most businesses don’t think of compliance as a cost-saving measure,” she explains. “They think of it as a burden. But, it is a cost-saving measure — in the short and long-term.”
What Is a Regulatory Compliance Policy?
A regulatory compliance policy is a statement from an organization — most often in writing — in which the entity establishes its commitment to following all laws and regulations and gives details on structures the company has put in place and practices it will follow to achieve compliance.
XpertHR’s Moakley says it is very important for a company to regularly and clearly communicate this policy to all employees. Companies should also collect electronic verifications from employees indicating that they’ve read and understood the policy, she adds.
“A business should communicate to its workforce, and to its leaders, what’s important: that this policy exists and that it reflects a culture that is important to an organization,” she explains.
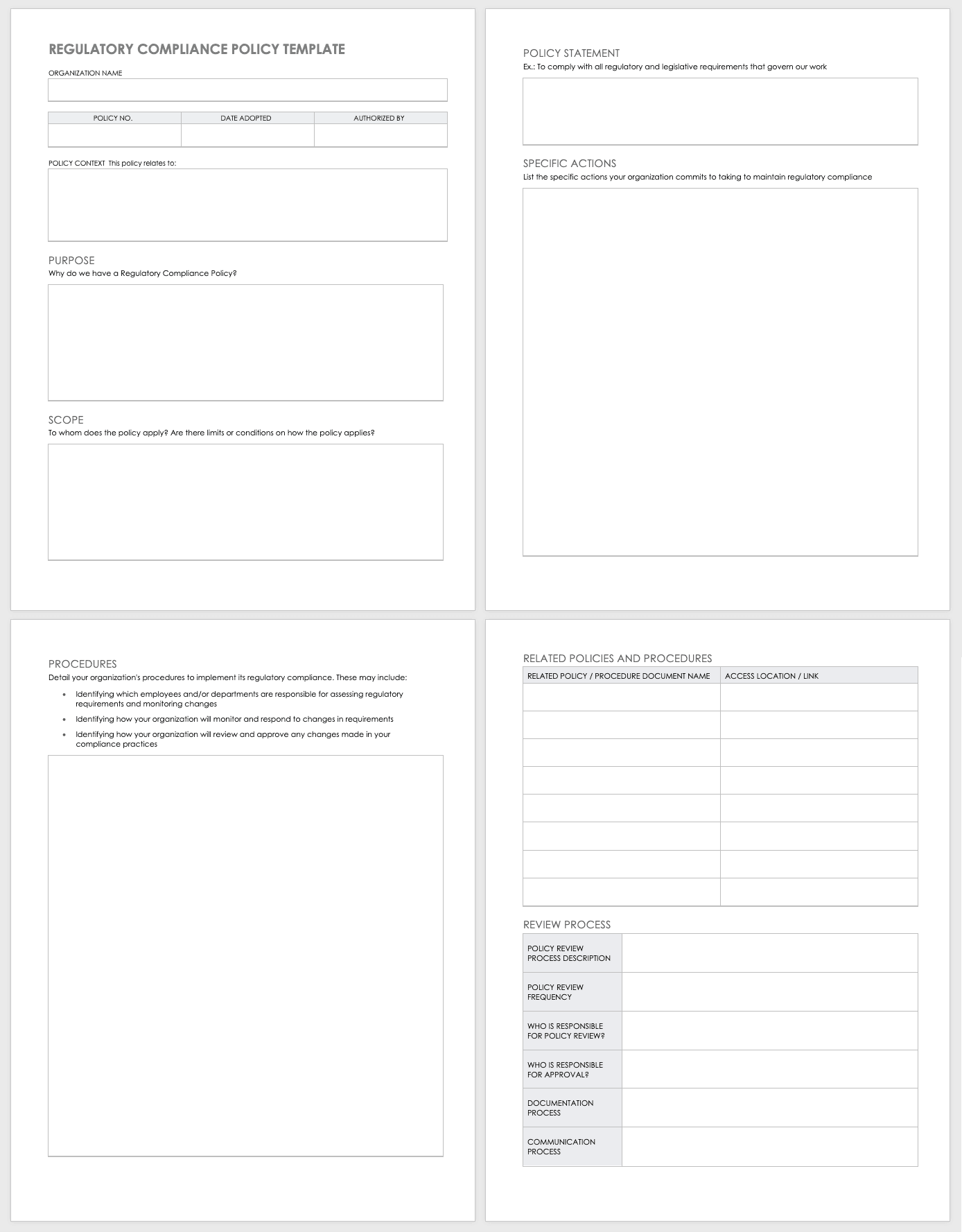
This template provides your organization with the basics to create a strong regulatory compliance policy. The pre-built template includes space for the main components of a policy document, including procedures and policies you will commit to follow. Additionally, the template includes questions your organization should answer to create a comprehensive regulatory compliance policy document.
Download Regulatory Compliance Policy Template
How to Stay on Top of Regulatory Compliance
It can seem overwhelming to understand and track all of the regulations that might apply to your company. But, there are basic steps that even smaller companies can take to stay on top of regulatory compliance:
- Assess Your Company’s Overall Exposure to Regulations: It’s important to understand whether or not your company is in a highly regulated industry (like healthcare, financial services, and insurance). If it is, you should begin by seeking outside advice from experts in your industry.
Even if your company is in a less regulated industry, use common sense about likely regulations. “If you’re preparing food, do you need to worry about food regulations?” asks Spark Compliance’s Grant-Hart. “Look at your company and think about what type of laws would naturally apply to it.” - Perform a Compliance Training Needs Assessment: The best way to understand and comply with regulations that affect your company is to train your employees. But, it may be cost prohibitive to train employees on every regulation that might apply to your company.
Moakley recommends performing the training needs assessment that might be most beneficial for your company. The assessment should include three categories, she says: areas that must be covered in the training; areas that would ideally be covered; and areas that may not be a good return on your company’s investment. “Your training needs analysis may recommend most of the need-to-haves and may have to forego some of the other areas,” she says. - Establish a Code of Conduct: Grant-Hart recommends that companies create a code of conduct document that lays out ethics that the company and its employees should adhere to. For example, the code might include provisions about the limit on the value of gifts an employee can accept from a business associate. It might also include provisions detailing protections against harassment in the workplace and protections for “whistleblowers” — employees who raise ethical issues about something the company or another company employee has done.
Grant-Hart recommends that as companies approach how they will deal with regulatory compliance, “they start with a code of conduct.” Such a code “tends to be the founding document for all compliance programs,” she says. - When Using and Adopting New Technologies, Always Consider the Regulations That May Apply to Those New Technologies: Don’t take it for granted that you’re already compliant just because you were compliant when using an earlier generation of a technology.
- Understand Where to Find Regulatory Information and How To Track Changes: A wide range of third-party services and software are available to help companies understand regulations. But, there’s also a large amount of accurate and free information, including from the government agencies that enforce the regulations, says Moakley.
She adds, “It’s important to view compliance as an ongoing process that you need to evaluate and tweak — based on business needs and a shifting legal landscape.”
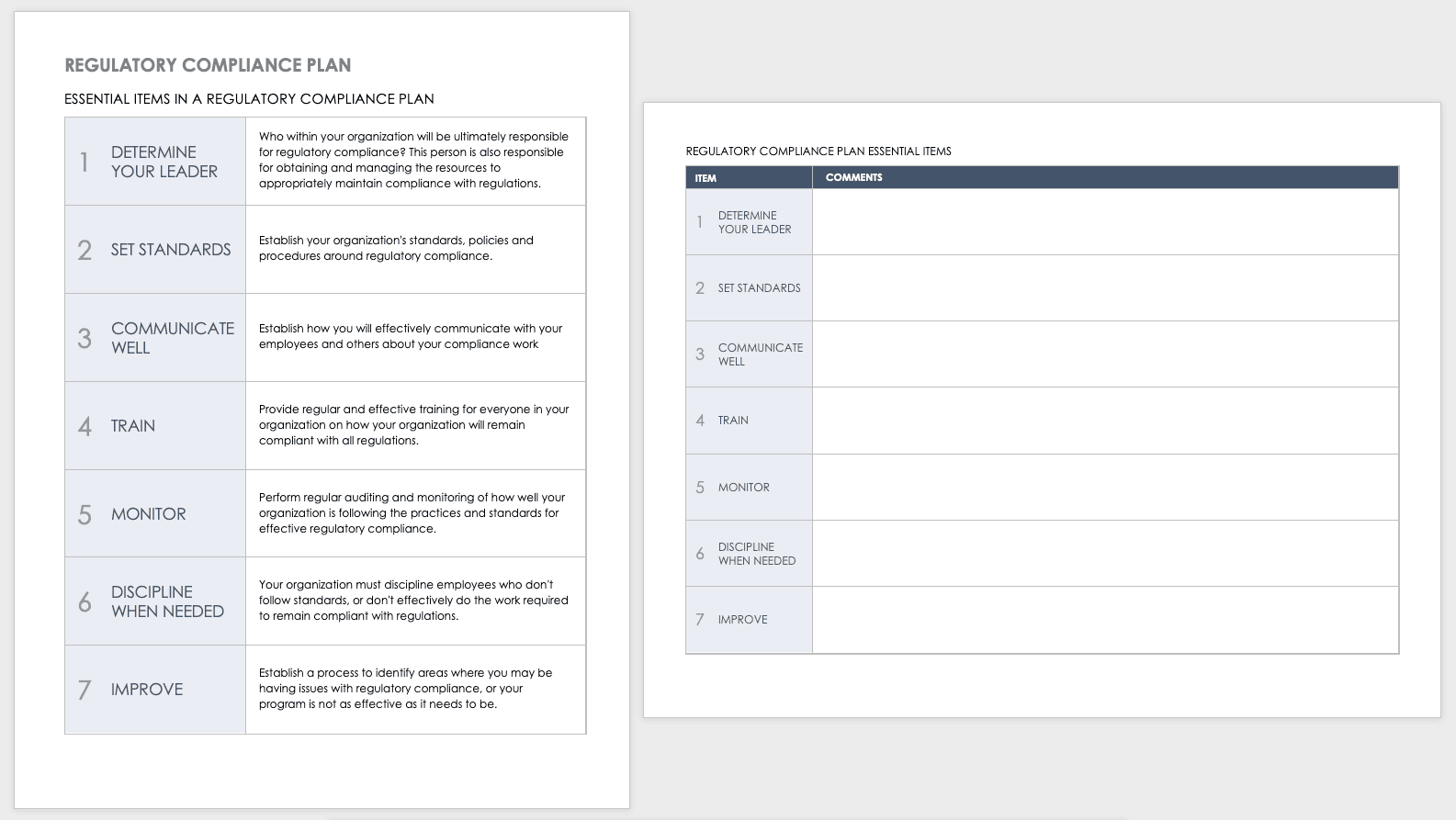
Use this template to outline the essential elements for a strong regulatory compliance plan. The template asks for details about your organization’s leadership, standards, communication strategies, training, employee discipline, and how it will continually improve its regulatory compliance.
Download Regulatory Compliance Plan Template
When Regulatory Compliance and Data Privacy Are at Cross-Purposes
Increasing demand for data privacy — and in some cases increasing regulations related to data privacy — can run counter to the demands for record-keeping concerning a number of other regulations. Here are two especially problematic areas:
- Data Retention: Many regulations require organizations to keep data for long periods of time, sometimes in ways that can make it difficult for companies to comply with data privacy regulations that impose strict limits on how businesses gather and store personally identifiable data.
- The “Right to Be Forgotten”: Data privacy laws often give people the “right to be forgotten” — meaning that organizations must destroy all personal data about an individual upon that individual’s request. Those rights can run counter to other regulations’ requirements that certain data be kept as evidence of compliance.
Organizational Strategic Issues to Consider Regarding Regulatory Compliance
Companies that are subject to a significant regulation need to consider how to structure their companies and processes to ensure they can operate well while also complying with regulations. Company leaders need to think about the following factors:
- How to predict the potential impact of regulations on the company’s strategic direction, its business goals, and its regulatory compliance processes
- How to balance the duties of compliance among legal, auditing, and other business functions
- How to encourage common compliance across different teams and company locations
- How to create internal systems that monitor and report on compliance
- How to measure the value of compliance, including in employee performance evaluations
Steps Organizations Can Take to Handle Regulatory Compliance
Larger companies and companies within highly regulated industries need to hire employees — sometimes dozens or even hundreds of employees — whose primary focus is the company’s regulatory compliance.
The Securities and Exchange Commission requires any company with publicly traded stock to have a compliance officer. The majority of such companies have regulatory compliance departments; some banks and other large companies have a compliance staff of hundreds.
Alternatively, smaller private companies may not even have one employee solely responsible for compliance. They may have a company lawyer or outside lawyer handle compliance. Or, a top company executive may be responsible. When it comes to smaller companies, Moakley advises, “it’s helpful to have a point person” who’s responsible for regulatory compliance.
Beyond staffing, companies can use software or undergo internal assessments to help with regulatory compliance. These options include the following:
- Acquiring Compliance Management Software: This helps organizations track the wide range of regulations that apply to all companies as well as those within specific industries.
- Developing a Business Continuity Plan: This involves determining how a company can continue to operate during and after a disaster, including a natural disaster, crash, virus, or other catastrophic event affecting a business’s information technology systems.
- Assessing Auditing Systems: This is an internal assessment that is crucial to maintaining regulatory compliance.
- Assessing and Improving the Security and Privacy of Information Technology Systems: This is also an internal assessment that is central to maintaining regulatory compliance.
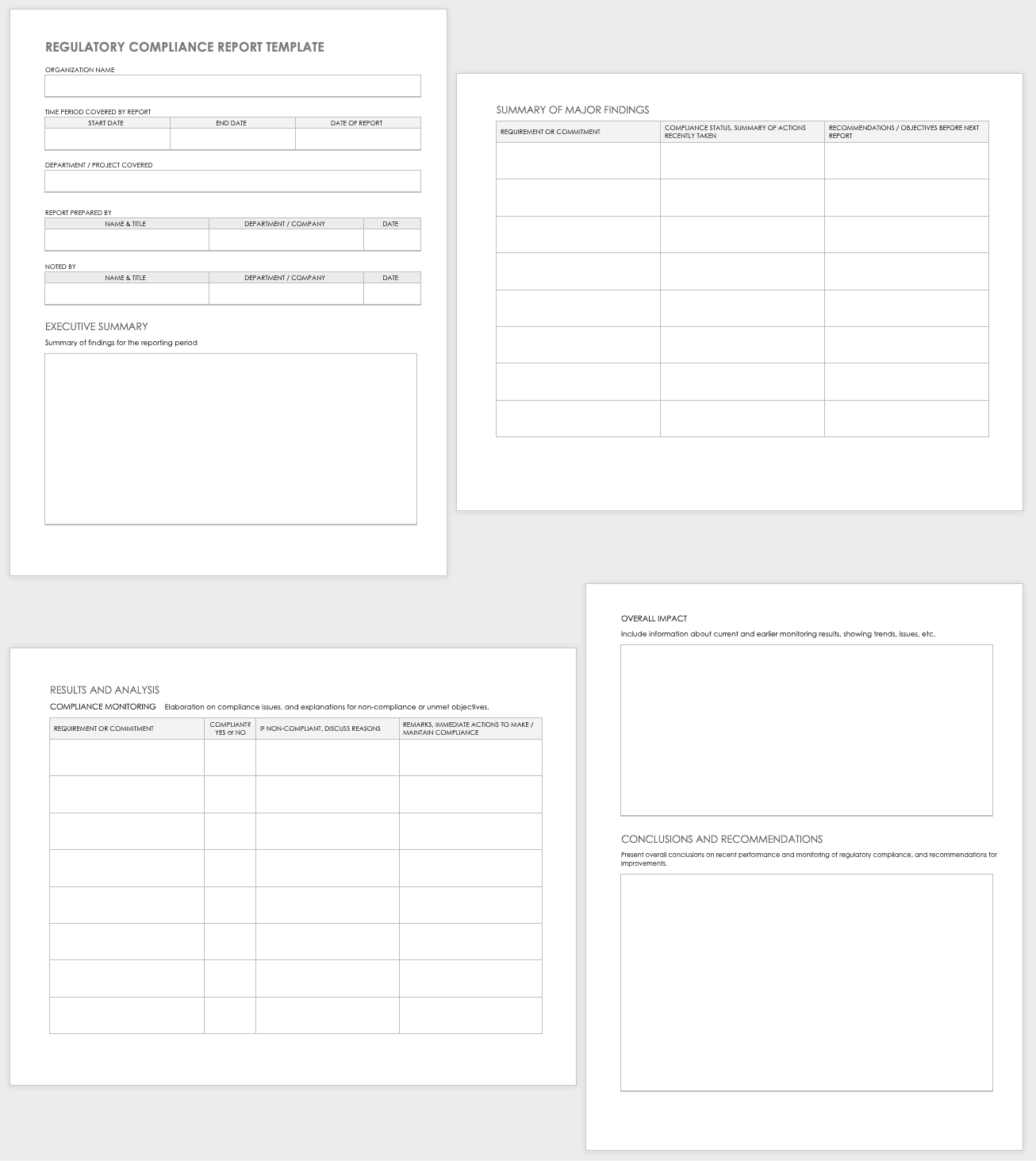
This pre-built template provides your organization with a structure to create periodic reports on your regulatory compliance work. The template asks for details on regulatory compliance requirements that apply to your organization, along with compliance status, a summary of actions taken, and recommendations for future actions.
Download Regulatory Compliance Report Template
Executive Positions That Regulatory Compliance Has Created
As regulations have increased in recent decades, larger organizations are increasingly hiring executives to fill specific compliance roles. Here are three of the most common positions:
- Corporate compliance officer
- Chief compliance officer
- Regulatory compliance officer
What’s Your Major? — “Regulatory Compliance”
As more companies hire executives and staff that focus on regulatory compliance, colleges and universities are taking notice. And, some colleges and universities have now established areas of study that are partially or entirely focused on regulatory compliance:
- Northwestern University’s School of Professional Studies in Chicago offers a Master’s of Science in Regulatory Compliance.
- Drexel University in Philadelphia offers a Graduate Certificate in Financial Regulatory Compliance, along with a Master’s of Legal Studies with a concentration in financial regulatory compliance.
- The University of Scranton in Pennsylvania offers a Master’s of Science in Human Resources Management that includes a significant focus on compliance issues.
FAQ: A Career in Regulatory Compliance Management
As more companies hire people for regulatory compliance work, and as colleges and universities offer majors that focus on compliance, more people are interested in understanding a potential career in compliance. Here are some of the most frequently asked questions about compliance managers:
What does a regulatory compliance manager do?
A regulatory compliance manager works to understand regulations that apply to an organization and sets up systems that help ensure the organization complies with those regulations. Alternatively, they work in governments that enforce regulations.
Where do regulatory compliance managers work?
Almost half of regulatory compliance managers work in federal, state, and local governments. The rest work in private enterprise and other organizations.
What is the average salary of a regulatory compliance manager?
In 2015, the median salary was $69,180.
What is the job demand for regulatory compliance managers?
In 2014, job demand was expected to grow about three percent per year between 2014 and 2024 — which was about half the national average for all jobs. Some believe that the growth of job opportunities in this industry might be slowing down as businesses increasingly use software and other technology to help with their regulatory compliance.
What are the educational requirements for a regulatory compliance manager?
The job requires a bachelor’s degree; a graduate degree might be beneficial if job growth is slow.
Benefits of Using an Outside Provider to Help with Your Company’s Regulatory Compliance
Many companies hire outside providers to help with regulatory compliance training or other compliance services. These providers may help smaller companies with much of their compliance work. But, the providers can also help the compliance departments of larger companies with specific tasks. Here are some of the benefits to hiring outside providers:
- They provide teams that are specialized and expert in specific industries and areas of compliance.
- They often have technical knowledge in a wide variety of areas.
- They use expert-developed risk methodologies and tools, which can help companies understand industry standards and best practices in a specific industry.
Services and Expertise of Regulatory Compliance Providers
Providers of regulatory compliance consulting can help your company in a number of ways:
- Help your company set up the design of a compliance program that routinely assesses risk and other compliance issues.
- Develop ways to embed your company’s compliance goals within the day-to-day operations of the business.
- Help your company understand and use technology to assist with compliance.
- Help your company track and adjust to continually changing compliance requirements.
- Conduct compliance and risk assessments.
- Help your company achieve an appropriate balance between compliance and risk, given limited budgets.
- Implement processes that help your company report its regulatory compliance.
Improve Regulatory Compliance with Real-Time Work Management in Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.